You might have heard about digital privacy. But do you truly know what it is exactly about? Digital privacy is …
Blog
Using Motomotar to Understand Car Security Features and Their Cost
India records over 1.5 lakh road accident deaths every year, according to government transport data. Safety matters, and knowing the tech that protects you on the road is critical before you buy. Airbags, ABS, electronic stability systems, and driver assistance tools are no longer luxury add-ons. They shape both survival rates and the final bill you pay at the dealership.
That is where Motomotar becomes useful. The platform breaks down features model by model, helping buyers see how safety tech affects pricing across cities. For example, when reviewing the Hyundai Creta, you can clearly compare variants, understand which trims include six airbags or advanced driver assistance systems, and see how those upgrades influence on road prices Delhi and other major markets.
Breaking Down Core Safety Technologies
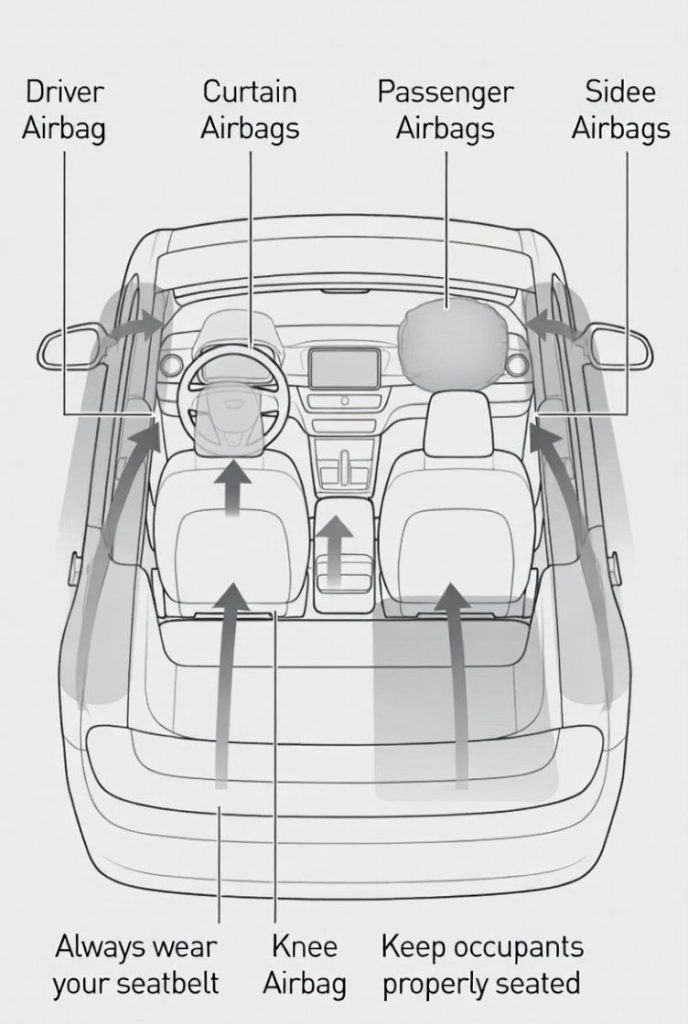
Car security features fall into two broad categories, passive and active safety. Passive systems reduce injury during a crash. Active systems help prevent a crash in the first place. Both impact vehicle pricing.
Passive Safety Features
- Airbags: Dual front airbags are now mandatory in India. Many cars offer side and curtain airbags in higher variants. Each additional airbag adds to manufacturing cost, which reflects in the ex-showroom price.
- Seatbelt pretensioners and load limiters: These tighten seatbelts during impact. They are standard in many mid-range models.
- Strong body structure: High-strength steel and reinforced crumple zones improve crash test ratings. Better crash scores often justify a higher price tag.
Adding four extra airbags can increase the variant price by several thousand rupees. While that seems significant, the long-term value in terms of safety is hard to ignore.
Active Safety Features
- ABS with EBD: Anti-lock braking systems prevent wheel lock during sudden braking. EBD balances brake force. This is standard in most modern cars.
- Electronic Stability Control: Helps maintain control during sharp turns or slippery conditions.
- ADAS: Advanced Driver Assistance Systems include lane assist, adaptive cruise control, and emergency braking.
ADAS features are usually offered in top variants. They can raise the price by a noticeable margin. Motomotar explains which variants include these features and whether the cost jump is justified for daily city driving or highway use.
How Safety Features Influence On Road Prices
Ex-showroom price is only part of the story. Registration charges, insurance premiums, and road tax shape the final on road prices Delhi buyers pay. Vehicles with higher ex-showroom prices attract higher taxes and insurance costs.
For instance, a mid variant of the Hyundai Creta may offer essential airbags and ABS at a reasonable cost. A top variant with ADAS and additional airbags can push the price higher by over a lakh rupees. That increase also raises insurance premiums because the insured declared value is higher.
Motomotar helps buyers compare these layers. Instead of looking at one number, you see the full ownership picture, including city-specific differences. Road tax in Delhi may differ from Mumbai or Bangalore, which means the same safety package can cost more or less depending on location.
Variation by Model and Market
Safety offerings vary widely across segments. Entry-level hatchbacks often stick to dual airbags and ABS. Compact SUVs and sedans may add side airbags and stability control. Premium SUVs introduce ADAS and 360-degree cameras.
Manufacturers also adjust features based on competition and demand in each market. Urban buyers often expect more technology. As a result, higher trims with advanced systems sell better in metro cities. Motomotar highlights these differences so you can see how one model compares to rivals in the same price band.
Another factor is Bharat NCAP crash ratings. Cars with strong safety scores tend to gain attention. When a model earns a higher rating, demand increases. Sometimes, updated versions come with improved structural safety, which can slightly raise the cost.
Are Advanced Features Worth Paying For?
The answer depends on your driving habits. If you drive mainly within city limits at moderate speeds, core features like ABS, multiple airbags, and stability control should be your priority. They offer strong protection without pushing the budget too far.
If you frequently travel on highways, ADAS features such as lane keep assist and forward collision warning add an extra layer of support. They reduce driver fatigue and help prevent human error. Because modern vehicles rely on connected electronics and software, it’s also important to understand protecting your vehicle’s security from cybercriminals so that these systems remain safe and effective. While such technologies increase the purchase price, they can lower accident risk.
When evaluating a model like the Hyundai Creta, it makes sense to compare mid and top variants carefully. Sometimes the price jump includes cosmetic upgrades along with safety tech. Understanding that split helps you decide whether you are paying for protection or appearance.
Practical Buying Tips for Safety-Focused Owners
- Check how many airbags are standard in the base variant.
- Review crash test ratings before shortlisting a car.
- Compare insurance costs between variants.
- Consider resale value, cars with better safety features often hold value well.
- Use Motomotar to compare city-wise pricing and feature lists side by side.
Safety technology shapes both your driving confidence and your financial commitment. Platforms like Motomotar make it easier to see beyond brochures and marketing claims. When you understand how features affect on road prices Delhi and in other cities, you make a smarter decision. Whether you choose the base or top version of the Hyundai Creta, the key is knowing exactly what you are paying for and why it matters.
Tech Launches & Cyber Conferences: Step & Repeat Banner Best Practices for NYC Tech Events

New York City hosts hundreds of tech events each year, from cybersecurity summits to groundbreaking product launches. These spaces are not just about ideas and innovation. They are about visibility, branding, and creating experiences that people remember long after the event ends. One subtle yet powerful tool that contributes to this visual storytelling is the step and repeat banner; a backdrop that brings together technology, design, and marketing.
At conferences where startups and tech giants share the stage, every detail counts. A crisp, professional backdrop featuring partner logos and sponsor names signals credibility and sophistication. That’s where Industri Designs step and repeat banners come into play. Their quality print materials and customizable options make them ideal for NYC’s fast-paced tech environment, where branding has to look sharp both on-site and on camera.
Why Step & Repeat Banners Matter for Tech Events
First impressions happen fast, especially in the tech world. Whether it’s a product unveiling, an AI demo, or a cybersecurity seminar, a well-designed step and repeat banner instantly elevates your event space. It serves as a visual hub where guests, executives, and media professionals gather for photos, helping to amplify brand visibility across social media platforms.
In NYC’s tech scene, branding is everything. These banners reinforce partnerships and sponsorships while giving every photograph a consistent professional background. When attendees share these images online, the banners extend your event’s reach beyond the venue, creating a ripple effect of engagement and awareness. For those interested in understanding the importance of technology for online shops, this same principle of digital visibility applies across industries — strong visuals and branding build credibility both offline and online.
Design Elements that Reflect a Tech Identity
Modern tech events demand visuals that match their futuristic themes. The right combination of fonts, colors, and materials can make a huge difference. Many NYC tech organizers now favor minimalist designs with clean typography, metallic tones, and high-contrast backgrounds. These elements not only enhance readability but also resonate with the sleek, forward-thinking image that defines the tech industry.
Lighting also plays a crucial role. Step and repeat banners should be printed on non-reflective materials to avoid glare under LED and stage lights. Matte vinyl or fabric finishes often work best, ensuring that logos remain crisp in photos and video recordings.
Maximizing Engagement Through Placement
Placement is just as important as design. The banner should be positioned in high-traffic areas like registration booths, photo zones, or near keynote stages. When attendees walk in, they should naturally encounter it, encouraging spontaneous photos and interviews. For multi-day tech conferences, organizers often use multiple smaller banners to create thematic zones throughout the venue, each highlighting a specific topic or sponsor.
Some companies even pair banners with digital backdrops or QR codes that link to live demos or apps, blending physical and digital experiences. This hybrid approach perfectly fits the interactive culture of tech events, where innovation and audience engagement go hand in hand.
Material and Print Quality: Why It Matters
Tech audiences have a sharp eye for detail. A poorly printed banner can instantly undermine an event’s professionalism. High-resolution printing and durable materials are non-negotiable. Using fade-resistant inks and tear-proof fabrics ensures that banners look just as good at the end of the event as they did at the start. This level of precision reflects the same attention to quality that tech brands expect from their own products.
Moreover, sustainability has become a growing concern in the tech industry. Many NYC companies now opt for eco-friendly printing processes and recyclable materials, aligning their event setups with corporate social responsibility goals. The right production partner understands these needs and offers environmentally conscious options without sacrificing visual impact.
Branding Beyond the Booth
A step and repeat banner can do more than just fill a backdrop. It can become a storytelling canvas that connects brands to their audiences. Some tech firms use them to display QR codes for product demos, app downloads, or giveaway entries. Others design modular banners that can be reused across events, saving time and cost while maintaining consistent branding.
For startups, the banner becomes a strategic branding tool. It helps smaller names stand alongside industry giants during photo ops, leveling the playing field in a space where visibility can drive partnerships and investor interest.
Final Thoughts
Every tech event tells a story of innovation, and visuals play a central role in that narrative. From cybersecurity expos to app launches, a step and repeat banner adds polish, purpose, and presence to any setup. When designed and produced thoughtfully, it becomes more than a photo backdrop, it becomes part of the event’s identity. Partnering with experts like Industri Designs step and repeat ensures that every print, finish, and layout reflects the cutting-edge spirit of NYC’s tech community.
For technology brands striving to make lasting impressions, the best banners don’t just display logos. They showcase vision, creativity, and the innovative energy that drives the city’s ever-evolving tech scene.
How Technology is Changing New Home Construction
 Technology is transforming the way we build homes. Today’s new houses by https://maykus.com/southlake/ are not just stronger or more energy-efficient. They are also becoming smarter and more secure. From the ground up, security is now a top feature in many construction plans.
Technology is transforming the way we build homes. Today’s new houses by https://maykus.com/southlake/ are not just stronger or more energy-efficient. They are also becoming smarter and more secure. From the ground up, security is now a top feature in many construction plans.
Built-in Smart Security
Gone are the days when a door lock and a porch light were enough. Many new homes now come with smart security systems already built in. These can include motion sensors, video doorbells, and smart locks that you can control from your phone. Builders work with security tech companies to install these systems during construction, so they’re ready the moment you move in.
This approach saves homeowners time and money. It also means these systems are hardwired into the house, not just added later. That makes them more reliable. Plus, they blend better into the home’s design, with no messy wires or visible equipment.
Technology That Protects
Aside from cameras and alarms, builders now use tech tools to improve safety in other ways. For example, new homes often include smart smoke detectors and carbon monoxide alarms. These can send alerts to your phone and contact emergency services if needed.
Another upgrade is smart lighting. This can be programmed to turn on at certain times or respond to movement. It helps make your home look occupied, even when you’re away. That’s a simple but effective way to prevent break-ins.
In some homes, sensors can also detect leaks or changes in temperature. These may seem like small details, but they help protect your home from water damage or electrical issues.
Planning for the Future
Builders know that homeowners want homes that are ready for the future. That’s why many are designing homes with tech in mind from the start. This includes wiring for internet-connected devices, smart speakers, and automation hubs. Some builders even offer custom security upgrades, depending on your needs.
This trend shows no signs of slowing down. With more smart devices coming to market, future homes may come with even more advanced safety tools. Think facial recognition at your front door or drones that patrol your yard.
It’s clear that security is no longer an afterthought. It’s becoming a standard part of new home construction. And with the help of smart technology, today’s homes are not just places to live — they’re built to protect.
5 Proven Tips to Increase Instagram Followers While Keeping Your Account Secure

Instagram is one of the most popular social media platforms, with over 1 billion monthly active users. With so many people vying for attention, standing out and growing your follower base can be daunting. However, growing your audience doesn’t have to come at the cost of security. You can build a thriving Instagram account without exposing yourself to risks by combining effective strategies with protective measures (source: 인스타 팔로워 늘리기 팁).
Optimize Your Profile for a Great First Impression
Your profile is your digital storefront. When someone visits your page, they first see your bio, profile picture, and content. To make a great first impression:
- Use a recognizable and high-quality profile picture. Whether it’s a logo or your face, ensure it reflects your brand or personality.
- Write a clear and engaging bio. Use keywords that represent your niche and include a call-to-action, like “Follow for daily tips on fitness.”
- Add a link. Utilize your bio link to direct followers to your website, blog, or other social platforms.
A well-optimized profile attracts followers and encourages them to engage with your content.
Use Relevant Hashtags Strategically
Hashtags are one of the best tools for getting discovered. However, not all hashtags are created equal. To use them effectively:
- Mix popular and niche hashtags. While trending hashtags have a broader reach, niche ones connect you to a targeted audience.
- Avoid banned or overused hashtags. These can harm your account’s visibility.
- Limit your hashtags. Instagram allows up to 30 hashtags per post, but using 5–10 well-chosen tags often yields better results.
The right hashtags increase your content’s reach and help attract followers interested in your niche.
Engage Consistently With Your Audience
Engagement is a two-way street. You must do the same if you want people to interact with your content. Here’s how:
- Reply to comments and messages. Show appreciation and keep the conversation going.
- Like and comment on other posts. Interacting with similar accounts can bring new eyes to your profile.
- Use interactive features. Polls, Q&A stickers, and story quizzes make followers feel involved and valued.
Building a strong relationship with your audience encourages them to share your content, attracting new followers organically.
Leverage Tools Like SNS Supporter for Account Growth and Security
Growing an Instagram account can take time and effort, but tools like SNS Supporter make the process easier and safer. Using tools strategically can help you automate tasks, track analytics, and enhance security. For example, SNS Supporter can assist in identifying the best strategies to grow your audience while keeping your account safe from phishing and hacking attempts.
When exploring tools like SNS Supporter, remember that protecting your account is just as important as growing it. Scams and hacking attempts are common, so stay vigilant.
Post High-Quality and Consistent Content
Consistency and quality are key to retaining and attracting followers. To ensure your content stands out:
- Stick to a theme or aesthetic. Whether it’s bright colors or minimalism, consistency helps establish your brand.
- Use high-quality visuals. Invest time in photography or design to create visually appealing posts.
- Post regularly. A predictable schedule keeps your account active and your followers engaged.
Don’t forget to experiment with different formats, like reels, stories, and carousels, to keep your audience interested.
Keep Your Account Secure
With Instagram’s growing popularity, account security has never been more critical. To protect your account:
- Enable two-factor authentication. This adds an extra layer of security to your login process.
- Avoid suspicious links or emails. Phishing scams are a common way accounts get hacked.
- Change your password regularly. Use a strong, unique password to minimize risks.
Your followers trust you to keep their data and interactions safe. Secure accounts also reduce downtime from recovering hacked profiles.
READ ALSO: Unmasking the Risks: Exploring the Tech and Security Implications of Buying Instagram Followers
Conclusion
Building an Instagram following requires a balance of creativity, strategy, and security. From optimizing your profile and using hashtags to engaging with your audience and leveraging tools like SNS Supporter, many ways exist to attract more followers. Always prioritize protecting your account from risks like phishing and hacking while you grow your presence. By following these proven tips, you can cultivate a loyal and engaged audience on Instagram.
Team Unity: Ensuring Security in Escape Room Team Building Experiences

Escape rooms have emerged as a popular team-building activity (check out team bonding in SG) in recent years, offering a unique and immersive experience for participants. As teams work together to solve puzzles and uncover clues, they not only strengthen their communication and problem-solving skills but also foster a sense of camaraderie and unity. However, in order for escape room experiences to be truly effective, it is essential to prioritize security and ensure the safety of all participants.
Creating a Safe Environment
The safety and well-being of participants should always be the top priority when planning and executing an escape room experience. This begins with meticulous planning and attention to detail in the design and construction of the room itself. All props, puzzles, and equipment should be carefully inspected to ensure they are safe and in good working condition.
Furthermore, escape room operators should conduct regular maintenance checks to identify and address any potential hazards or safety concerns. This includes checking for loose or damaged objects, ensuring proper ventilation and lighting, and implementing emergency procedures in case of accidents or emergencies.
Staff Training and Supervision
In addition to creating a safe physical environment, it is also important to invest in staff training and supervision to ensure the smooth and secure operation of the escape room experience. Staff members should be well-trained in emergency response procedures and equipped to handle a variety of situations, including medical emergencies, fire drills, and evacuations.
Furthermore, staff members should be actively engaged in monitoring and supervising participants throughout the experience to prevent accidents or injuries. This includes providing clear instructions and guidance, enforcing safety rules and regulations, and stepping in to intervene if necessary.
Participant Safety Guidelines
To further enhance security and safety, it is important to establish clear guidelines and rules for participants to follow during the escape room experience. This includes providing safety briefings before the start of the activity, outlining potential risks and hazards, and instructing participants on how to safely navigate the room.
Additionally, participants should be encouraged to communicate with each other and with staff members if they encounter any safety concerns or issues during the experience. This open line of communication can help to identify and address problems quickly, ensuring the overall safety and enjoyment of all participants.
Other related article: Unmasking the Risks: Exploring the Tech and Security Implications of Buying Instagram Followers
Conclusion
In conclusion, prioritizing security and safety is essential in creating a successful and effective escape room team-building experience. By investing in meticulous planning, staff training, and participant guidelines, escape room operators can create a safe and enjoyable environment for teams to work together and build unity. By taking these important steps, we can ensure that every participant has a memorable and rewarding experience.
The Intersection Of Technology & Security In The Pneumatic Fittings Manufacturing Industry
In the fast-paced world of manufacturing, technology and security play a vital role in ensuring efficiency, productivity, and safety. As industries evolve and embrace advancements, the pneumatic fittings manufacturing sector has also witnessed a significant impact. Today, pneumatic fittings manufacturer uses cutting-edge technology and robust security measures to optimize their operations and safeguard their valuable assets.
The Role of Technology in Pneumatic Fittings Manufacturing
Pneumatic fittings manufacturers are increasingly turning to automation to streamline their production processes. Advanced robotics and intelligent machinery are employed to handle repetitive tasks with precision and speed. Automated systems can assemble fittings, test their functionality, and perform quality checks, minimizing errors and reducing production time. This not only increases efficiency but also enables manufacturers to meet growing demands while maintaining consistent quality standards.
With the advent of big data and advanced analytics, pneumatic fittings manufacturers can extract valuable insights from their operations. By analyzing data collected from various sources, including machinery, production lines, and quality control systems, manufacturers can identify patterns, trends, and potential bottlenecks. This data-driven approach empowers decision-makers to optimize production schedules, minimize downtime, and implement predictive maintenance strategies, thereby improving overall equipment effectiveness (OEE) and reducing costs.
The Importance of Security in Pneumatic Fittings Manufacturing
Protecting Intellectual Property
Intellectual property (IP) is a valuable asset for pneumatic fittings manufacturers. From innovative designs to proprietary manufacturing processes, safeguarding IP is crucial for maintaining a competitive edge. Robust security measures, such as restricted access to sensitive information, encrypted communication channels, and surveillance systems, help prevent unauthorized access and protect valuable trade secrets. By prioritizing security, manufacturers can preserve their unique innovations and maintain market leadership.
Mitigating Cybersecurity Risks
As technology becomes more integrated into manufacturing processes, the risk of cybersecurity threats increases. Pneumatic fittings manufacturers must take proactive measures to mitigate these risks and protect their digital infrastructure. Implementing firewalls, intrusion detection systems, and secure authentication protocols can help defend against external attacks. Regular software updates, employee training programs, and strict access control policies further enhance cybersecurity resilience and ensure the integrity of critical systems.
Conclusion
In the dynamic world of pneumatic fittings manufacturing, the convergence of technology and security is transforming the industry. By embracing automation, IoT connectivity, and data analytics, manufacturers can optimize their processes, increase efficiency, and drive innovation. Simultaneously, robust security measures protect intellectual property, mitigate cybersecurity risks, and ensure occupational safety. As the industry continues to evolve, the seamless integration of technology and security will play a pivotal role in shaping the future of pneumatic fittings manufacturing, allowing manufacturers to stay ahead of the competition while delivering reliable and high-quality products.
The Technology Powering the Modern Movie Domain
A complicated web of coding, encryption, and bandwidth optimization is operating behind the scenes with each and every click on the movie title. The film industry, particularly websites like 123 movies, testifies to the redefinition of entertainment globally due to the innovativeness of the security and streaming technology. What used to be available only in the form of physical DVDs and TV channels, now transformed into a highly advanced AI-powered mechanism. The goal is to provide instant high quality streaming experiences to millions of users all over the world.
Digital Streaming and Data Security
With the rapidly increasing online viewership, privacy and data safety have become the most important aspects in the world. The current movie streaming websites are heavily based on encrypted servers, secure sockets and user authentication systems to protect sensitive data.
- Encryption also keeps the identity of viewers secret and also helps to stop unauthorized access of copyrighted content.
- Cybersecurity specialists are quietly withholding around the clock to detect breaches and apply patches to keep the confidence and meet international data standards.
This is a security layer that will help the audience to watch their favorite movies without fearing privacy leak, malware, or identity theft. These have been problems that had bedeviled the dawn of digital streaming.
Artificial Intelligence and Recommendation System
The domain of movies has been revolutionized by artificial intelligence regarding the level at which users engage in interaction. Machine learning is used to recommend engines that can be used to suggest individual lists of titles based on watch history and preferences by genres and even time of the day. This improves user satisfaction and it can also assist streaming services to maintain the audience longer because there is less decision fatigue.
It concerns an increasing problem of the age of unlimited digital options.
The Trade-Off between Convenience and Security
Responsibility goes with accessibility. Cyber threats and scams are also a possibility due to the same technology which lets millions of people stream high-definition movies. Users are advised to be careful of browsing sites that are not known, suspicious links and should check the use of the SSL certificates before clicking the play button. Ethical technology behavior, such as the use of VPNs and software updates, can help to make the streaming process smooth and safe.
 Finally, there is safety and fun. The film industry performs well when users remain updated and vigilant of their online health.
Finally, there is safety and fun. The film industry performs well when users remain updated and vigilant of their online health.
Tech Reads to Explore
To the reader wanting to dig deeper into the science of safe entertainment, read posts about the ones that are connected to online privacy using VPN. These articles unravel the invisibility of the technology surrounding your screen at any time you press the play button.
Summary: Where Technology and Entertainment Intersect
The film industry is literally the marriage of creativity and entertainment. It incorporates data science, encryption and artificial intelligence to provide smooth streaming experiences that are entertaining and safe. As evidenced by websites like 123 movies, technology has reached a new height where people can download movies clumsily and fast, in a high-quality and can be accessed anywhere in the world.
However, awareness is required with much convenience. Being considerate of internet security means that this new wizardry will be as entertaining as it is respectable. With streaming continually changing, it is increasingly obvious that the future of cinema is no longer going to be limited to theaters but is embedded in the digital code of technology itself.
Protecting Client Privacy: Cybersecurity Tips for Cleaning Businesses
 Cleaning professionals handle more sensitive information than most people realize. From client addresses and alarm codes to payment details and staff schedules, there’s a steady flow of data that, if compromised, could put both the business and its clients at risk. In an age where cyber threats are becoming more sophisticated, cleaning companies can’t afford to overlook cybersecurity.
Cleaning professionals handle more sensitive information than most people realize. From client addresses and alarm codes to payment details and staff schedules, there’s a steady flow of data that, if compromised, could put both the business and its clients at risk. In an age where cyber threats are becoming more sophisticated, cleaning companies can’t afford to overlook cybersecurity.
Here are practical ways to protect client privacy and strengthen your digital security.
1. Recognize the Value of Client Data
Even if your business is small, client information is valuable. Hackers often target smaller companies because they tend to have weaker security measures. Treat every piece of data, from contact details to invoices, as sensitive. Make sure all employees understand the importance of safeguarding it. This mindset is the first step in building a strong cybersecurity culture.
2. Use Strong Password Practices
Hackers often break into accounts using weak or reused passwords. Make sure your team uses strong, unique passwords for every system. A secure password mixes letters, numbers, and symbols, and avoids common words or patterns. Encourage using a password manager to store them securely, rather than writing them down or reusing the same password across platforms. Change passwords regularly and update them immediately if there’s any suspicion of a breach.
3. Secure Your Devices
Cleaning teams often use mobile devices to manage schedules, client addresses, and payment apps. Each phone, tablet, or laptop connected to your system can become a doorway for hackers. To minimize risks:
- Require passwords, PINs, or biometric locks on all devices.
- Install antivirus software and firewalls.
- Use mobile device management (MDM) tools if you have a team.
Small steps like these can stop unauthorized access before it starts.
4. Limit Access to Sensitive Information
Use role-based permissions so employees only see the data they need to do their job. For example, field staff might only need client names, addresses, and service details, rather than payment history or billing information. This approach limits exposure if an account or device is compromised.
5. Encrypt Communication and Data
Whenever possible, encrypt client data, both when stored and when sent. Use secure, encrypted email or messaging systems for sharing client details. If your business keeps records in the cloud, make sure your provider offers end-to-end encryption. This ensures that even if data is intercepted, it can’t be read without the encryption key.
6. Watch Out for Phishing Scams
Phishing is still one of the easiest ways hackers steal information. Common red flags include urgent language, spelling mistakes, or unexpected requests for login information. Encourage employees to verify messages directly with the sender before responding or clicking any links.
7. Keep Software and Systems Updated
Regularly update operating systems, apps, and security tools. Enable automatic updates whenever possible. Don’t forget about smaller devices like tablets or scheduling apps; they can be just as vulnerable as computers.
8. Protect Wi-Fi Networks
Your office or mobile hotspot network should be secure, encrypted, and password-protected. Change the default name and password on your router, and avoid using public Wi-Fi for business activities. If staff need to access company systems while on the go, use a virtual private network (VPN) to protect their connection.
9. Store Data Responsibly
Only keep the data you actually need. The less information you store, the less there is to protect. Establish clear retention policies. Delete old client information, outdated payment records, and unnecessary files. When disposing of old devices, make sure data is completely wiped or the hardware is physically destroyed.
10. Have a Response Plan Ready
Even with the best precautions, no system is entirely immune to cyber threats. Create a response plan so your team knows exactly what to do in the event of a breach. The plan should include:
- Who to contact (IT support, clients, law enforcement)
- Steps to secure systems and prevent further damage
- How to notify affected clients
Having a clear protocol helps you respond quickly and maintain client trust.
11. Train Your Staff Regularly
Cybersecurity isn’t just a one-time setup. Threats evolve constantly, so training should be ongoing. When employees understand how their actions affect client privacy, they’re more likely to stay vigilant.
12. Partner with Trusted Vendors
If your business uses third-party apps for scheduling, invoicing, or communication, make sure those vendors follow strong security practices. Please review their privacy policies and data protection measures. Ask how they handle encryption, storage, and access control. A single weak link in your vendor chain can expose your client data.
Protecting client privacy isn’t just about compliance; it’s about trust. Clients invite your team into their homes or workplaces, often giving access to private spaces and sensitive details. Showing that you take their privacy seriously can set your business apart. By following these cybersecurity best practices, you safeguard your reputation, strengthen client relationships, and build a company that’s both secure and reliable.
Gangnam Jjim-O Homepage Security as a Guide to Personal Cybersecurity Protection
The Gangnam Jjim-o homepage (강남 쩜오 홈페이지) incorporates advanced security protocols to protect client privacy and maintain the confidentiality that defines premium hospitality services. They recognize that online security directly impacts customer trust and business reputation. Hence, it is integral to implement multiple layers of protection including:
- Encrypted communications
- Secure payment processing
- Robust data management systems
Professional websites handling sensitive client information must maintain the highest security standards to prevent unauthorized access, data breaches, and privacy violations. If compromised, customer safety and business can be at risk. The establishment’s commitment to digital security reflects broader industry recognition that cybersecurity has become essential for protecting both business operations and customer relationships. These same principles of proactive protection, multi-layered security, and constant vigilance that safeguard business websites apply directly to personal cybersecurity practices that individuals must adopt to protect their digital lives from increasingly sophisticated online threats.
Understanding Modern Cyber Threats
Cybercriminals employ diverse tactics to access personal information, financial accounts, and digital devices through phishing emails, malicious websites, and social engineering techniques designed to exploit human psychology rather than technical vulnerabilities. Attack methods evolve constantly as security measures improve, requiring ongoing education and adaptation to recognize new threats before they cause significant damage to personal or financial security.
Strong password creation involves combining random words, numbers, and symbols in patterns that resist automated cracking attempts while remaining memorable for legitimate users. Length proves more important than complexity for password strength.
Password managers generate and store unique passwords for every account, eliminating the security risks associated with password reuse while simplifying login processes through encrypted auto-fill capabilities.
Authentication Method Diversity

Text message verification provides basic second-factor protection, though authenticator applications offer superior security against SIM swapping attacks that intercept SMS messages through telecommunications vulnerabilities. Hardware security keys represent the most secure authentication method, using cryptographic protocols that cannot be duplicated or intercepted remotely, making them ideal for protecting high-value accounts.
Secure Communication Practices
Email encryption ensures that message contents remain private during transmission and storage, preventing unauthorized access even if communications are intercepted or email accounts are compromised.
Messaging applications with end-to-end encryption protect conversation privacy from service providers, government surveillance, and criminal access attempts that target centralized communication platforms.
Network Security Management and Software Maintenance
Home router security requires changing default passwords, enabling automatic firmware updates, and configuring guest networks that isolate visitor devices from personal computers and smart home equipment. Public Wi-Fi protection involves using virtual private networks (VPNs) to encrypt internet traffic when connecting through untrusted networks in cafes, hotels, airports, and other shared connectivity environments.
Operating system updates include security patches that address newly discovered vulnerabilities, making prompt installation essential for maintaining protection against emerging threats that target unpatched systems.
Application updates often contain security improvements alongside new features, requiring regular maintenance schedules that balance convenience with protection needs for all installed software programs.
Data Backup and Recovery Planning
Regular backup schedules protect against ransomware attacks, hardware failures, and accidental deletion by maintaining current copies of important files in separate, secure locations that cannot be accessed by malware or unauthorized users.
Cloud storage security requires understanding provider encryption practices, access controls, and geographic data storage locations to ensure backup systems meet personal privacy and security requirements. Recovery testing verifies that backup systems function correctly before emergency situations arise, preventing data loss through inadequate preparation or system failures during critical moments.
Gangnam Jjim-O Home Page Mirrors the Flexibility of Remote Work
The way people seek experiences has transformed in the digital age. Just as many turn to luxury and premium discreet entertainment through the Gangnam Jjim-O home page (강남 쩜오 홈페이지), others are also navigating the changes that come with online accessibility in their personal and professional lives.
Technological evolution put emphasis on how it continued to shape people’s lives from convenience, flexibility, and privacy. The same dynamics that attract individuals to digital platforms also explain why remote work has become a central part of modern careers, reshaping the daily realities of professionals everywhere.
Adjusting to the New Normal of Remote Work
Remote work has shifted from being a rare perk into a common standard for many industries. Employees now conduct meetings from their living rooms, manage projects from shared co-working spaces, and connect across time zones with ease. Commuting is becoming a thing of the past as remote work creates real flexibility. However, it creates a blurred line between professional, and personal life. Learning to separate these boundaries has become one of the greatest challenges in sustaining both productivity and mental well-being.
Gangnam Jjim-O Home Page as a Reflection of Online Adaptation
Much like exclusive platforms built for tailored experiences, remote work demands adaptability and intentional design. A digital environment becomes an extension of how people function and achieve their goals. Crafting a workspace at home that encourages focus, whether through ergonomic furniture, noise reduction, or scheduled breaks, mirrors the importance of personalization.
Just as a premium service is curated for satisfaction, remote work succeeds when individuals curate their surroundings to suit their needs.
Balance between Flexibility and Discipline

One of the strongest advantages of remote work is flexibility. Without discipline, it quickly turns into distraction. Professionals are now learning that success requires more than simply working from home. Establishing routines, setting start and end times, and prioritizing tasks are crucial for productivity. Flexibility must work hand in hand with discipline to create a sustainable balance that prevents burnout while still embracing freedom.
Technology as the Core of Connection
The reality of working remotely would not exist without digital tools. Video conferencing, project management platforms, and instant messaging applications bridge the gap between physical distance and professional collaboration.
Caution must be practiced as that same technology we used also introduces the risk of over-connection. This makes employees feel constantly available. Finding balance requires using these tools intentionally, ensuring that convenience does not replace the need for healthy boundaries.
Impact on Work-Life Integration
Remote work has created a shift in how individuals view time and priorities. Parents may find more moments with their children, while others can pursue hobbies once lost to commuting hours.
This integration also means that professional demands sometimes spill into personal spaces, making it harder to fully disconnect. Developing strategies such as clear communication with colleagues and dedicated off-screen activities helps restore balance and keep personal lives intact.
What’s ahead of doing Remote Work?
As organizations experiment with hybrid setups, employees are discovering new ways to redefine productivity and satisfaction. Remote work is not just a temporary adjustment but an evolving structure that challenges traditional office culture.
Success depends on striking harmony between independence and collaboration, while recognizing that flexibility will remain a cornerstone of professional life. The future promises more innovation, but the essence lies in how individuals adapt and embrace the change.
Why Curated Links Are Vital for Online Safety in 2025

Cyberattacks have skyrocketed, with a reported 82% increase in 2024 alone. The internet, while a treasure trove of knowledge, hides dangers like phishing, malware, and fake websites. Curated links act as trusted guides, steering users toward safe destinations. These carefully vetted directories filter out harmful sites, offering a lifeline in the chaotic digital world. How do they work? By applying strict verification processes, ensuring every click leads to security.
The Role of Curated Directories
Directories are the gatekeepers of the web. Directory platforms or address collection sites like JusoJura in Korea (source: 주소주라) meticulously verify websites before listing them. They check for secure connections, scan for malicious code, and confirm legitimacy. This process shields users from scams while providing access to reliable resources, from streaming services to forums. Regular updates keep these lists current, and user guides on spotting threats enhance their value. Why trust them? Their transparency fosters a community where safety comes first.
Battling Phishing Scams
Phishing remains a relentless threat. These attacks trick users into sharing sensitive information through deceptive links mimicking trusted sites. Curated directories fight back by using advanced tools to verify site authenticity. They check SSL certificates and monitor user reports to catch fakes early. “A single click can cost you everything,” warns a cybersecurity expert. By relying on curated links, users bypass the traps, making browsing a safer adventure.
Blocking Malware Risks
Malware hides in plain sight. It sneaks into devices through shady downloads or scripts on unverified pages. Curated link directories counter this by running rigorous scans before listing sites. They use antivirus tools and manual checks to ensure cleanliness. Ever wondered why some searches lead to trouble? Curated lists eliminate that risk, offering categorized, safe options for every need, from education to entertainment.
Exposing Fake Platforms
Fake websites are masters of disguise. They mimic popular platforms to steal data or money. Curated directories excel at spotting these impostors by cross-referencing against known frauds and leveraging community feedback. This vigilance saves users from falling for too-good-to-be-true deals. Hesitant to click? With curated links, that fear fades, as each site is vetted for authenticity. As scams evolve, these directories use AI to stay one step ahead.
Empowering Users Through Education
Knowledge is a powerful defense. Beyond listing safe links, many directories offer tutorials on spotting secure sites, using VPNs, and keeping software updated. This education builds confidence for independent browsing. “Safety starts with knowing what to avoid,” shares a user on a tech forum. By blending practical tools with learning, curated directories create a robust shield against digital threats.
The Strength of Community Collaboration
Communities fuel safer browsing. Users contribute by reporting suspicious links or suggesting new ones, keeping directories accurate and relevant. In 2025, with online activities like remote work and shopping at an all-time high, this collective effort is crucial. It transforms individual caution into a shared mission. Ready to join in? Exploring a directory connects you to this network of trust.
Adapting to Future Threats
The digital world never stands still. Emerging technologies like quantum computing may bring new risks, but curated directories are ready. They invest in cutting-edge tools to detect threats faster. Whether you’re a parent, a professional, or a casual browser, these resources offer peace of mind. The future of online safety hinges on staying proactive, and curated links lead the way.
READ ALSO: Value of Cybersecurity in the 21st Century
A Call to Safer Browsing
Curated links are more than tools—they’re essentials. They weave a safety net for our digital lives, guiding us through a landscape riddled with risks. By choosing verified paths, we take control of our online journey. So, next time you surf the web, let curation light the way. Safety is just a trusted link away.
The Tech-Savvy Future of Pressure Washing and Water Services
Pressure cleaning, often referred to as a washing service, has evolved dramatically from the days of basic garden hoses and manual scrubbing. In the modern era, this industry leverages cutting-edge technology to deliver efficient, eco-friendly, and secure cleaning solutions. Whether it’s revitalizing a residential driveway, maintaining a commercial property, or restoring a towering building façade, pressure cleaning services now incorporate smart innovations that enhance performance, conserve resources, and prioritize safety. These advancements are transforming how we maintain cleanliness in both private and public spaces.
The integration of technology into pressure cleaning has made it possible to tackle tough cleaning challenges with precision. From graffiti removal to industrial equipment maintenance, modern pressure washers are equipped with features that optimize performance while minimizing environmental impact. This technological revolution is not only about aesthetics but also about sustainability and efficiency, ensuring that surfaces remain pristine without compromising the planet’s resources.
Innovative Water Services: Smarter, Safer, Greener
Water is the lifeblood of pressure cleaning, and advancements in water management technology have significantly improved the industry’s efficiency. Smart nozzles, for instance, automatically adjust water pressure based on the surface being cleaned—whether it’s delicate wood, sturdy concrete, or fragile glass. High-efficiency pumps deliver powerful cleaning with minimal water usage, reducing waste while maintaining effectiveness. Some advanced systems even incorporate greywater recycling, allowing used water to be filtered and reused, further promoting sustainability.
Real-time monitoring systems are another game-changer. Technicians can now track water pressure, temperature, and chemical levels through digital dashboards, ensuring optimal performance for each job. These innovations not only reduce the environmental footprint but also enhance the quality of the cleaning process. For example, in regions facing water scarcity, such technologies are invaluable, enabling businesses and homeowners to maintain clean surfaces without exacerbating resource shortages.
Tech Meets Security in Pressure Cleaning
While security may not immediately come to mind when thinking of pressure cleaning, it’s a critical consideration in commercial and high-stakes environments. Modern pressure cleaning equipment now features advanced security measures, such as GPS tracking and tamper-proof access systems, to protect valuable machinery from theft or unauthorized use. Remote shut-off capabilities further enhance equipment safety, allowing operators to disable units instantly if a security breach is detected.
In sensitive locations like data centers, military bases, or corporate headquarters, pressure cleaning crews are managed with digital identity verification and scheduling software. These systems ensure that only authorized personnel access restricted areas. Additionally, integration with surveillance systems and access logs provides an extra layer of oversight, ensuring that cleaning operations align with stringent security protocols. This focus on security is particularly crucial in industries where downtime or breaches could have significant consequences.
Looking Ahead: The Future is Automated
The future of pressure cleaning lies in automation, which is already making waves in the industry. Robotic cleaners are increasingly used for large-scale or hazardous tasks, such as cleaning skyscraper exteriors, bridges, or industrial rooftops. These robots reduce the need for workers to operate in dangerous conditions, improving safety while maintaining efficiency. Equipped with sensors and AI, robotic cleaners can navigate complex surfaces and deliver consistent results.
As the pressure cleaning industry continues to evolve, we can expect even more intelligent tools and systems. Innovations like AI-driven cleaning schedules, predictive maintenance for equipment, and fully autonomous cleaning fleets are on the horizon. These advancements will further enhance the industry’s ability to deliver cleaner, safer, and more sustainable results. The future of washing services is not just about removing dirt—it’s about creating smarter, greener, and more secure cleaning solutions that meet the demands of a rapidly changing world.
Smart Cleaning: How Technology Ensures Safe and Efficient Air Conditioner Maintenance in Brisbane

Air conditioners collect dust, mold, and bacteria more quickly than most people realize. Poorly maintained systems not only reduce cooling efficiency but can also affect indoor air quality. That’s why more Brisbane homeowners are leaning on tech-driven cleaning solutions to keep their air conditioners safe and running at peak performance.
Advanced Clean Air is leading this change by using innovative tools and systems that remove the mess and guesswork. Their fast and reliable air conditioner cleaning services in Brisbane are powered by advanced scheduling tech and trained professionals who understand how to get the job done right, every time.
High-Tech Tools, Cleaner Air
Gone are the days of manual scrubbing and uncertain results. Advanced Clean Air relies on high-pressure cleaning systems, eco-safe disinfectants, and precision instruments to thoroughly clean the interior of air conditioning units. These tools don’t just remove visible dirt—they kill mold spores, bacteria, and allergens hidden in coils and filters. Similar tech-infused cleaning services in Singapore are also reshaping how homes and businesses approach hygiene, proving that innovative tools can deliver spotless results worldwide.
The process is fast, efficient, and most importantly, safe. Each technician is equipped with state-of-the-art vacuums and flush kits, ensuring thorough cleaning without damaging the internal components. No water leaks, no foul smells, and no leftover residue—just a fresh, cool breeze.
Digital Scheduling for Hassle-Free Appointments
Time is valuable, and Advanced Clean Air gets that. Their online booking platform makes it easy for customers to schedule appointments without needing to make a phone call. Customers can view available slots, select the time that works best for them, and receive instant confirmation. It’s all about removing barriers to service and giving people control over their maintenance needs.
Additionally, automated reminders help reduce the number of missed appointments. It’s one less thing for customers to worry about, especially during peak summer months when systems are running around the clock and breakdowns become more common.
Skilled Technicians You Can Trust
Technology is only as good as the hands that use it. That’s why Advanced Clean Air invests heavily in training its technicians. Each team member is certified, background-checked, and trained on both the tools and the etiquette of in-home service. They arrive on time, in uniform, and ready to explain what they’re doing before they even touch the unit.
This transparent communication builds trust. Customers know they’re not just getting a quick clean—they’re getting service from professionals who take pride in their work. The combination of technology and transparency makes a significant difference, especially for families or businesses that require dependable service.
No Surprises—Only Clean Results
Transparency is at the core of what Advanced Clean Air does. Their pricing is transparent, with no hidden fees or upselling during the visit. Before starting, technicians walk customers through the scope of work, and once done, they show the results using before-and-after photos.
These visuals are more than proof—they’re peace of mind. Clients can see the difference and know their system is clean, efficient, and safe to use. And because the company tracks service history, repeat customers can benefit from ongoing maintenance schedules tailored to their unit’s needs.
Serving Brisbane Homes and Beyond
From older Queenslander homes to new apartment blocks, Brisbane has a wide range of air conditioning systems. Advanced Clean Air adapts to all of them. Their innovative diagnostic tools can identify system types and potential problems before the cleaning even begins, allowing for customized service across different brands and models.
This versatility is what makes their service stand out. Whether you’re dealing with wall-mounted splits, ducted systems, or even commercial-grade setups, our team has the tools—and the expertise—to clean them safely and thoroughly.
The Smart Choice for Cleaner Living
Smart cleaning isn’t just about high-tech gadgets. It’s about creating a seamless, stress-free experience from booking to final result. Advanced Clean Air is showing Brisbane what modern maintenance should look like: digital convenience, expert care, and lasting results. That’s why more residents are turning to them not just for cleaner air, but also for peace of mind.
How Online Liquor Stores Like The Barrel Reserve Keep Your Orders Safe and Secure

Online shopping for alcohol has become a convenient option for many. With just a few clicks, you can have your favorite whiskey or wine delivered to your door. But how do these platforms ensure your orders are safe and secure? Modern eCommerce sites, like The Barrel Reserve, use advanced technology to protect customers. From age verification to secure payments, they prioritize safety while keeping the shopping experience smooth. Let’s explore how these systems work and why they matter.
Age Verification Done Right
The rise of the online liquor store has transformed how people buy alcohol. Platforms like The Barrel Reserve combine convenience with strict safety measures. For starters, they tackle one of the biggest concerns in alcohol sales: age verification. Laws require buyers to be 21 or older in the U.S., and reputable sites enforce this rigorously. The Barrel Reserve, for instance, uses robust digital tools to confirm a customer’s age. These systems often involve uploading identification documents or integrating third-party verification services. Some even use AI to cross-check data, ensuring only eligible buyers can place orders. This step protects both the business and the consumer, keeping underage sales at bay.
Secure Payment Gateways
Beyond age checks, secure payment gateways are a cornerstone of safe online shopping. When you enter your credit card details, you want assurance that your information won’t fall into the wrong hands. The Barrel Reserve employs encryption technologies like SSL (Secure Sockets Layer) to safeguard transactions. This means your data is scrambled into unreadable code during transmission, making it nearly impossible for hackers to intercept. Additionally, trusted payment processors—think Stripe or PayPal—add another layer of security. These systems use tokenization, replacing sensitive card details with unique codes, so your information stays protected even if a breach occurs.
Protecting Your Personal Data
Customer data protection goes beyond payments. Personal details like your name, address, and purchase history are goldmines for cybercriminals. The Barrel Reserve takes this seriously, using advanced cybersecurity measures. Firewalls, intrusion detection systems, and regular security audits help keep their databases secure. They also comply with data protection laws like GDPR for international customers or CCPA for California residents. This ensures your information isn’t misused or sold without consent. Ever wonder why you’re asked to create an account with a strong password? It’s not just a formality—it’s a frontline defense against unauthorized access.
Human Oversight and Fraud Prevention
But security isn’t just about tech. Human oversight plays a role too. The Barrel Reserve trains its staff to spot suspicious activity, like unusual order patterns that might signal fraud. For example, if someone tries to place multiple high-value orders from different locations using the same account, red flags go up. Manual reviews can catch what automated systems might miss. This blend of technology and human vigilance creates a robust safety net, giving customers peace of mind.
Secure Delivery Matters
What about delivery? Alcohol isn’t like ordering a t-shirt—there are strict regulations. The Barrel Reserve partners with licensed carriers who verify the recipient’s age at the door. This ensures your bottle of bourbon doesn’t end up with a minor. Some platforms even use GPS tracking to monitor shipments in real-time, reducing the risk of theft or loss. If a package goes missing, customer support teams are quick to resolve issues, often offering refunds or replacements. This focus on secure delivery keeps the process trustworthy from start to finish.
Stopping Fraud in Its Tracks
Fraud prevention is another key piece of the puzzle. Ever heard of chargeback fraud? It’s when someone claims they didn’t receive their order and wants a refund while keeping the product. The Barrel Reserve uses tools like address verification systems (AVS) to confirm that billing and shipping details match. They also monitor for unusual activity, like rapid-fire orders from a single IP address. These measures protect both the business and honest customers, ensuring prices stay fair and operations run smoothly.
Why Trust Matters
Why does all this matter? Trust is everything in eCommerce, especially when buying alcohol online. A single data breach or underage sale can damage a company’s reputation and lead to hefty fines. The Barrel Reserve invests heavily in security to maintain customer loyalty. Their seamless interface hides the complex systems working behind the scenes, letting you focus on choosing the perfect bottle. Whether it’s a rare scotch or a local craft beer, you can shop confidently knowing your data and order are protected.
READ ALSO: How Technology is Enhancing Security in Rehabilitation Treatment Centers
Looking Ahead
The future of online alcohol sales looks even more secure. Innovations like blockchain for supply chain transparency or biometric age verification are on the horizon. For now, platforms like The Barrel Reserve set the standard. They prove that convenience doesn’t have to come at the cost of safety. Next time you browse for a bottle online, take a moment to appreciate the tech keeping your order secure. It’s a lot more than just a click—it’s a system built on trust and protection.
The Impact of Digital Media on Emergent Literacy Skills
Children as young as two years old now engage with digital media daily. Whether through interactive storybooks, educational apps, or online videos, technology has become part of early learning environments. These tools shape how kids develop the foundational skills for reading and writing—what educators call emergent literacy skills.
While books, crayons, and alphabet blocks still play a role, digital tools are deeply embedded in children’s language learning. A detailed breakdown of this development can be found in the Ultimate Guide to Emergent Literacy Skills for Kids, highlighting how new technologies support early childhood education.
Opportunities Brought by Digital Tools
 Digital media offers interactive experiences that traditional print materials can’t always provide. E-books with read-aloud features, word highlighting, and animations help children connect sounds with letters. Apps designed for phonics and vocabulary allow repeated practice, which reinforces learning in a fun and engaging way.
Digital media offers interactive experiences that traditional print materials can’t always provide. E-books with read-aloud features, word highlighting, and animations help children connect sounds with letters. Apps designed for phonics and vocabulary allow repeated practice, which reinforces learning in a fun and engaging way.
Young learners can now access stories in multiple languages, watch characters act out storylines, or tap on objects to hear their names and sounds. These interactions build vocabulary and comprehension, essential pieces of emergent literacy. Children also develop listening and attention skills when engaging with structured digital activities, especially those that include feedback or require decision-making.
The Role of Parental and Teacher Involvement
Research shows that the positive impact of digital tools depends largely on how they are used. A tablet filled with games won’t help a child learn to read if no one is there to guide them. Parents and educators who actively engage with children during screen time—asking questions, encouraging responses, and expanding on ideas—can turn passive consumption into active learning.
For example, reading an e-book together and pausing to ask, “What do you think will happen next?” helps children think critically. It also mimics traditional shared reading practices that build vocabulary, narrative skills, and print awareness. Combining technology and adult support turns digital time into meaningful learning time.
Challenges and Concerns
Despite the benefits, there are valid concerns about the overuse of digital media. Too much screen time can limit opportunities for physical play, face-to-face communication, and hands-on exploration—all of which are important for early development. Children need a balance of activities that engage their bodies and minds differently.
Another concern is content quality. Not all digital apps labeled “educational” truly help develop literacy. Some offer flashy visuals without much substance. Others may be loaded with ads or include features that distract from learning. That’s why parents and educators must be selective and intentional about the media children consume.
Finding the Right Balance
Experts agree that digital tools should be used to complement—not replace—traditional forms of learning. Paper books, storytelling, drawing, and playing with letters or magnetic words remain essential. Blending digital and non-digital experiences to support children’s curiosity and growth is key.
Scheduled screen time, co-viewing with adults, and engaging in real-world follow-up activities—like acting out a story read on a tablet or writing a simple letter after a phonics game—can deepen a child’s understanding of language and symbols.
READ ALSO: Roblox and How It Can Be Safe for Our Kids
Looking Ahead
As technology continues to evolve, so will its role in early literacy. Voice-activated devices, AI-driven learning platforms, and personalized content may open new doors for emergent readers. But no matter how advanced these tools become, the human element remains irreplaceable.
Children learn language best through rich interactions—talking, listening, asking questions, and telling stories. Digital media should support, not substitute, those moments. With thoughtful use and adult guidance, it can be a powerful ally in helping young minds develop a love for reading and writing from the very beginning.
The Role of IoT in Monitoring and Maintaining Heating Systems

Smart homes are no longer a futuristic dream. They’re now a part of daily life for many, and heating systems are one of the biggest beneficiaries of this shift. Thanks to the Internet of Things (IoT), managing indoor temperature has become smarter, faster, and far more efficient.
IoT-enabled heating systems use sensors and connected devices to collect and send real-time data. This data helps monitor temperature changes, detect faults early, and optimize energy use automatically. Companies like Sanichauffe already take charge by offering innovative heating solutions that prioritize comfort and safety.
How IoT Changes Heating System Management
Traditional heating systems rely heavily on manual input. You set a temperature and hope the system keeps up. There’s little room for fine-tuning, especially if you’re not home. With IoT, every part of the heating process can be adjusted on the fly. Whether on the couch or at the office, you can control your system using a mobile app or voice command.
IoT sensors can track internal and external temperatures, humidity levels, and system performance. These devices can also learn your habits over time. For example, if you typically raise the heat at 7 AM before heading to the shower, an innovative heating system will remember and automate this action without being asked.
Safety and Real-Time Alerts
Safety is another significant benefit. Heating systems, especially those that rely on gas or oil, can be dangerous if not maintained properly. IoT tools help reduce this risk. They can detect unusual behavior, such as unexpected temperature drops or pressure spikes, and send instant alerts to homeowners and technicians.
This real-time feedback makes it easier to stop minor issues from becoming bigger, more expensive problems. For instance, if a boiler shows early signs of failure, the system can automatically notify a professional for inspection before it breaks down.
Energy Efficiency and Cost Savings
Efficiency is where IoT shines. Traditional systems often run longer than necessary, wasting energy and money. IoT devices optimize heating schedules by adjusting output based on occupancy and outdoor weather. This not only keeps your home warm but also lowers your bills.
Some systems even offer reports showing how much energy you use and where you can cut back. Over time, this transparency helps families become more energy-conscious, reducing their carbon footprint and utility expenses.
Examples of IoT Integration
Let’s look at some real-world use cases. A smart thermostat connected to an IoT network can sync with your smartphone’s GPS. As you head home, the system can automatically start heating your house to your preferred temperature. By the time you walk through the door, everything feels just right.
Another example is predictive maintenance. Devices installed by brands like Sanichauffe monitor system health constantly. They don’t just wait for problems—they anticipate them. That means fewer breakdowns, less downtime, and peace of mind for homeowners.
The Future of Heating Is Connected
As technology improves, IoT heating systems will become even more intuitive. They’ll sync better with solar panels, bright windows, and weather apps to create complete climate control ecosystems. They’ll work silently in the background, learning your preferences and adapting automatically.
We’re heading toward a future where heating systems do more than just heat. They’ll protect your home, lower your energy use, and provide real-time insights that help you make smarter choices. For households looking to stay ahead, investing in IoT-based heating is no longer a luxury—it’s a necessity.
READ ALSO: Protecting Every Home Making Use of the Latest in Technology
Final Thoughts
IoT is transforming how we interact with our heating systems. It brings a new level of convenience, safety, and efficiency. Whether through real-time alerts or energy-saving automation, connected heating solutions are here to stay. Companies like Sanichauffe are paving the way with systems that don’t just respond—they think ahead.
How Technology and Security Shape Modern Sports Broadcasting
 The world of Free sports broadcast (source: 무료스포츠중계) has been transformed by advancements in technology. Fans today enjoy a viewing experience that is more immersive and secure than ever before. From high-definition video to real-time data analysis, technology has revolutionized how sports are shared with the world. However, with these advancements come new challenges in security, ensuring that both broadcasters and viewers remain protected.
The world of Free sports broadcast (source: 무료스포츠중계) has been transformed by advancements in technology. Fans today enjoy a viewing experience that is more immersive and secure than ever before. From high-definition video to real-time data analysis, technology has revolutionized how sports are shared with the world. However, with these advancements come new challenges in security, ensuring that both broadcasters and viewers remain protected.
Technology’s Role in Sports Broadcasting
Technology has taken sports broadcasting to new heights. High-definition (HD) and ultra-high-definition (UHD) cameras capture every detail of the game, making fans feel like they are part of the action. Innovations like virtual reality (VR) allow viewers to experience games from unique perspectives, such as a player’s point of view or even from inside a stadium.
Artificial intelligence (AI) is also playing a big role. AI-driven tools analyze gameplay in real-time, offering instant replays and detailed statistics. This provides commentators and viewers with deeper insights into the strategies behind each move. Technology has not only enhanced how we watch sports but also how we understand them.
Security Challenges in Modern Broadcasting
As technology evolves, so do the risks associated with broadcasting. Cybersecurity is a major concern for sports broadcasters, especially with the rise of live-streaming platforms. Hackers can disrupt live events, steal sensitive data, or illegally stream content. This threatens the integrity of broadcasts and the revenue generated through official channels.
To combat these issues, broadcasters are investing in secure streaming platforms. These systems use encryption to protect live feeds and prevent unauthorized access. Digital watermarking is another tool being used to track and identify the source of pirated content. These measures ensure that viewers can enjoy their favorite games without worrying about interruptions or breaches.
The Future of Sports Broadcasting
The integration of technology and security will continue to shape the future of sports broadcasting. 5G networks promise faster and more reliable streaming, even in crowded stadiums. Cloud computing will make it easier to store and manage vast amounts of video footage and data.
Security measures will also improve, with AI helping to detect and respond to threats in real-time. Biometric authentication, such as facial recognition, could enhance the safety of live events and broadcasts alike. These advancements will provide fans with an unmatched experience while keeping content creators and broadcasters protected.
Technology and security are the driving forces behind modern sports broadcasting. As they continue to evolve, fans can look forward to even more engaging and secure ways to enjoy their favorite sports.
The Intersection of Technology and Security in Auto Repair
 Technology has revolutionized many industries, and auto repair by AutotronicsPA is no exception. Modern vehicles are equipped with advanced systems that make driving safer and more comfortable. However, these advancements come with challenges, especially in terms of security. Understanding how technology plays a role in both fixing cars and protecting them can help vehicle owners stay informed.
Technology has revolutionized many industries, and auto repair by AutotronicsPA is no exception. Modern vehicles are equipped with advanced systems that make driving safer and more comfortable. However, these advancements come with challenges, especially in terms of security. Understanding how technology plays a role in both fixing cars and protecting them can help vehicle owners stay informed.
Advanced Tools for Accurate Repairs
Today’s auto repair shops rely on high-tech tools to diagnose and fix problems. Mechanics use devices like OBD (On-Board Diagnostics) scanners to read error codes from a vehicle’s computer. These codes provide detailed information about engine performance, electrical systems, and more. This technology makes diagnosing issues faster and more accurate.
For example, if your car’s check engine light comes on, a mechanic can use an OBD scanner to identify the issue in minutes. This efficiency saves both time and money. Additionally, tools like digital torque wrenches and thermal imaging cameras ensure repairs are precise, reducing the chances of future problems.
Cybersecurity for Connected Vehicles
Modern cars are not just machines; they are also computers on wheels. Features like GPS navigation, Bluetooth connectivity, and Wi-Fi hotspots enhance convenience but also expose vehicles to cyber risks. Hackers can potentially access a car’s system, controlling its locks, engine, or even brakes.
Automakers and repair shops are working together to address these risks. Many newer vehicles have security updates similar to those on smartphones. Repair shops that specialize in advanced systems can update your car’s software to protect it from cyber threats. For car owners, it’s essential to regularly check for updates and use trusted service providers.
Combining Technology and Expertise
Even with advanced tools and systems, technology can’t replace human expertise. A skilled mechanic understands how to use these tools effectively and can spot problems that machines might miss. For example, a scanner might detect a fuel efficiency issue, but a mechanic’s experience can reveal underlying causes like a clogged fuel injector. This combination of technology and expertise ensures your car is not only fixed but also optimized for performance and safety.
How to Stay Ahead
To keep your vehicle in top condition, be proactive about maintenance and security. Regular checkups at a trusted auto repair shop will ensure your car’s systems are updated and functioning properly. Additionally, ask your mechanic about cybersecurity measures for connected vehicles. Small steps like securing your car’s Wi-Fi network with a strong password can make a big difference.
Technology has transformed auto repair, making it more efficient and reliable. At the same time, staying informed about security risks can help you protect your vehicle from potential threats. By combining regular maintenance with a focus on safety, you can enjoy the benefits of modern technology without worry.
Buying Gmail Accounts Can Elevate Engagement, but How?
Businesses now rely on Gmail for effective marketing, reaching target audiences, enhancing customer engagement, and streamlining communication. Buying Gmail accounts offers efficiency and better segmentation, though it also introduces privacy and security concerns. Companies must balance the advantages of technology with robust data protection to secure online spaces and maintain trust.
Understanding Cyber Threats
Modern technology brings conveniences but also risks. Cyber threats, including malware and phishing schemes, have evolved as cybercriminals exploit vulnerabilities in software and networks. The growth of digital networks increases the potential for attacks, making cybersecurity awareness crucial.
Threats like ransomware, which locks data for ransom, and IoT-based attacks highlight the importance of proactive security measures.
Considerations when Buying Gmail Accounts
Encryption is crucial for digital security, converting sensitive information into code readable only by authorized users. It’s essential for online shopping, mobile banking, and personal communications, helping businesses protect customer data and meet regulatory standards, especially in healthcare and finance. However, adequate security also requires regular updates and security controls.
Importance of Multi-Factor Authentication (MFA)

Multi-factor authentication (MFA) enhances security by directing users to verify their individuality through considerable steps, such as documenting passwords and confirming a code sent to their mobile device. MFA adds layers to the login process, making accessing accounts harder for unauthorized users. Implementing MFA on social media, email, and banking apps strengthens security for individuals and protects sensitive business data. It’s a simple yet effective step for better digital security.
Staying Safe with Regular Software Updates
Software updates are important for security, as they address vulnerabilities that hackers could exploit. Regular updates for operating systems, browsers, and applications help protect today’s threats. Staying current is vital for businesses’ cybersecurity. Automated updates and security audits can enhance network safety and reduce cyber incident risks.
Individuals and companies should routinely check and apply updates to defend against emerging threats.
As technology advances, cybersecurity must evolve, too. While cyber threats remain, users and organizations can protect their digital assets through knowledge, vigilance, and proactive measures. Staying informed, using tools like encryption and MFA, and committing to regular updates fosters a safer digital environment. Investing in cybersecurity brings peace of mind and opens up secure opportunities for connection.
Exploring the Intersection of Technology, Security, and the Providence of Safari Adventures in Tanzania

Experiences in African safari Tanzania are unparalleled, offering breathtaking views of the Serengeti, the majestic Mount Kilimanjaro, and the awe-inspiring Ngorongoro Crater. Modern safaris, like the Providence Safari, now integrate advanced technology and heightened security measures to ensure travelers enjoy not only the stunning landscapes but also the comfort of safety, seamlessly blending adventure with peace of mind.
Enhancing Safety Through Real-Time Tracking and Monitoring
One of the biggest challenges in the safari industry is maintaining a balance between preserving natural habitats and integrating technology to enhance safety. Providers like Providence Safari leverage satellite tracking for real-time monitoring of safari vehicles and routes, allowing guides and guests to stay connected in remote areas. GPS-enabled devices guide guests across Tanzania’s sprawling national parks, where orientation can easily be lost. This level of monitoring is instrumental for security, especially in emergencies when guests might require swift medical assistance or evacuation.
Digital Identification for Personal Safety
Further enhancing security are digital identification systems used by many safari operators. These systems allow guests to register personal information and share travel details with safari providers before the trip. By having access to critical data, companies like Providence Safari can prepare for emergencies, manage logistics efficiently, and ensure personalized safety plans for each traveler.
Drones: A New Perspective on Wildlife Safety
Drone technology has become a game-changer in enhancing safety and providing a unique perspective on wildlife. When used with permits, drones offer aerial views of animal herds and landscapes, capturing rare moments without disturbing the animals. This technology is particularly useful in minimizing risky human-animal encounters by maintaining a safe observational distance.
Communication Tools for Quick Response Times
Communication tools like two-way radios and satellite phones provide an essential line of contact in case of emergencies, ensuring quick response times. Many safari vehicles are now equipped with Wi-Fi hotspots, giving travelers and staff a digital safety net even in Tanzania’s most remote areas.
Embracing Technology for a Safer, Sustainable Safari Experience
As African safari adventures evolve, providers like Providence Safari are setting industry standards by using technology to balance adventure with robust security measures. This approach not only improves guest safety but also supports conservation efforts, enabling travelers to experience Tanzania’s wild beauty responsibly.
The Role of Webdesign Konstanz in Functionality and Security
Webdesign konstanz has evolved to reflect the growing demand for modern, user-friendly websites that captivate visitors and prioritize functionality. As businesses aim for a solid online presence, web design must prioritize user experience and security. Protecting sensitive data is crucial in today’s digital age.
Webdesign Konstanz in the Face of Cybercrime
With the expansion of the internet and reliance on technology, cyber threats have surged. Hackers use advanced techniques to breach security measures and access sensitive information, leading to significant financial losses. The world is expected to lose $10.5 trillion annually to cybercrime by 2025, highlighting the critical requirement for solid security measures.
Innovations in Security Technology

The technology sector has responded with innovative security solutions to these growing threats. Artificial Intelligence and Machine Learning utilize data analysis to recognize patterns and identify anomalies, allowing immediate response to threats. Security systems driven by AI learn from previous incidents to enhance defenses, creating challenges for hackers attempting to infiltrate networks. Biometric authentication methods improve security by allowing only authorized access to sensitive information and systems.
The Role of Blockchain in Security
Blockchain technology is also making waves in security. Initially developed for cryptocurrencies like Bitcoin, blockchain offers a decentralized approach to data storage. Decentralization ensures that data is not stored in a single location, making it difficult for hackers to compromise. Industries like finance and healthcare are using blockchain to enhance security.
Smart contracts automate processes and securely record transactions, fostering trust among users and stakeholders.
Best Practices for Personal Security
While technology continues to evolve, individuals can take proactive steps to protect their personal information. Regularly updating passwords, using two-factor authentication, and employing password managers can help minimize cyber threats. Educating oneself about potential threats, such as phishing scams, is crucial for staying informed and cautious.
Embracing a Secure Future
As technology advances, the relationship between innovation and security will remain paramount. Organizations and people must adopt a proactive security strategy, leveraging the latest technologies to avoid potential threats. By prioritizing security measures and fostering a culture of awareness, we can confidently navigate the ever-changing landscape of technology.
Embracing the synergy between technology and security protects sensitive information and empowers individuals and businesses to thrive in an increasingly digital world. With a commitment to innovation and a focus on security, we can look forward to a safer, more secure future.
Tech-Savvy Game Days: How Streaming Security Enhances Sports Broadcasting
Sports fans, rejoice! Gone are the days of scrambling for cable packages or battling the remote. Today, cutting-edge technology brings the thrill of live games directly to your devices, transforming every day into a potential game day. But with this convenience comes a crucial responsibility: securing your streaming experience.
Behind the Scenes: The Tech Powering Sports Broadcasts
Have you ever wondered how a live game seamlessly appears on your screen? It’s a complex dance of technology. Cameras capture every action on the field, sending high-definition video signals to a central hub. From there, sophisticated editing software stitches everything together, adding commentary, graphics, and replays. Finally, powerful encoders compress the signal for efficient transmission over the internet, reaching your device for real-time viewing. This intricate process, known as sports broadcasting, relies heavily on secure infrastructure to deliver a smooth and uninterrupted experience. Check out more on the technical aspects of sports broadcasting on RoyalTV.
Securing Your Stream: Why Encryption Matters
Now, let’s talk about the invisible force protecting your game day enjoyment: encryption. Imagine the broadcast signal as a coded message. Encryption scrambles that message, making it unreadable to anyone without the decryption key. This ensures that your viewing experience stays private and secure. Hackers or unauthorized users attempting to intercept the signal would only see a jumbled mess, effectively safeguarding your data and preventing malicious activity.
Choosing a Secure Platform: Your Ticket to a Safe Game Day
With many streaming services offering live sports, choosing the right one is key. Look for platforms that prioritize security. Here are some tell-tale signs:
-
Strong encryption standards: Look for platforms that utilize industry-standard encryption protocols like AES-128 or AES-256. These provide robust protection for your data.
-
Two-factor authentication: This adds an extra layer of security by requiring a second verification code when logging in, further safeguarding your account.
-
Transparent security practices: Reputable platforms will clearly outline their security measures on their website. Look for information on data protection and privacy policies.
By opting for secure platforms and staying vigilant, you can ensure your game days are filled with electrifying action, not security worries. So, grab your favorite snacks, settle in for the game, and let technology take care of the rest, knowing a secure digital shield protects your streaming experience.
Innovative Security Features of GRABE Pumps that Shape Industrial Technology

Safety and efficiency in the field of industrial operations are greatly required as tasks deal with machinery. GRABE Pumps and Industrial Equipment Ltd. (GRABE Bombas e Equipamentos Industriais Ltda) has grown its profile on appreciation due to the advanced security technology it employs.
Considering that the GRABE pumps are used in nearly all sectors, they are credited for their sophistication in safety measures, which are redefining industrial safety systems.
Below are some of the top reasons that safe and secure make GRABE pumps the pumps of choice.
Automated Devices for Pump Shut-Down Operation Maintenance
This automated system monitoring GRABE pumps operates based on data and is pre-programmed to shut down operations to prevent overheating, leaks or any other danger.
This means that should a situation be noticed, every possible operation in the business ceases at once, which saves risks as well as damages and time as well.
Real-Time Monitoring
Warranty of avoiding malfunctions in GRABE pumps also involves the monitoring of the levels of fluids and pressure in real time.
GRABE pumps are specially constructed to apply into the monitoring systems whereby even when the pump is operational, the pump system can be expected to communicate to the operator abnormal circumstances and enhance quick changes by relieving or pumping safety valves.
Such coupling reduces risks thanks to incorporating further measures into processes instead of abolishing them.
Anti-Corrosion Coating
Most of the industrial mechanical pumps are normally mounted in places that have the chances of being washed with chemicals. GRABE Pumps are also designed with a coating of anti-corrosion, which improves safety due to leak prevention and extends the useful life of the equipment.
This is an important feature for the technological improvement of safety and effectiveness.
ALSO READ: Protecting Your IPTV Subscription: Understanding Security Risks and Best Practices
Design for the Prevention of Explosion
In industries which use combustible materials, GRABE pumps are made with an explosion-proof feature for maximum protection. This presents an additional level of protection in environment that is hazardous and minimizes incidents.
Backup System within the Pumping Units
In the case of power outages, GRABE pumps have integrated emergency backup systems that provide an operational or safe shutdown capability. This is extremely important in those areas where even small interruptions in performance lead to tragedies.
Conclusion
The security features provided by GRABE Pumps and Industrial Equipment Ltd are in many cases more than additional safety; rather, they help to advance industrial technology.
With the help of implementing these systems, industries can ensure that the operations take place smoothly in a safe environment.
Email Writer AI: Your Key to Effective Communication
Effective communication is vital for businesses to thrive. And one of the most common forms of business communication is through emails. However, crafting the perfect email can be a time-consuming and sometimes daunting task. But fear not, because a revolutionary solution has arrived – Clippit AI, an artificial intelligence platform that is set to revolutionize the way we write emails. With its advanced algorithms and natural language processing capabilities, Clippit AI takes email writing to a whole new level, making your communications more powerful and impactful than ever before.
-
Advanced Algorithms and Machine Learning

AI-powered email writers utilize advanced algorithms and machine learning to analyze patterns and predict effective communication strategies. This innovative technology enables businesses to streamline their email writing process and optimize their communication efforts. With the help of email writer AI, you can create compelling and persuasive emails in a matter of minutes, saving you valuable time and energy. With clippit AI, you can just enter a phrase to start and it will continue to create the body of your message in an instant. Try it out!
-
Enhanced Quality of Communication

Not only do AI email writers save time, but they also enhance the quality of your communication. These algorithms have been trained on vast datasets and are continually improving to provide more accurate and personalized suggestions. By harnessing the power of AI, you can ensure that your emails are engaging, concise, and tailored to your specific audience.
-
Consistent Brand Voice and Conversations
 AI email writers can help businesses maintain consistency in their brand voice and messaging. By analyzing previous email interactions and understanding your unique style, AI algorithms can generate content that reflects your company’s values and resonates with your recipients. This level of personalization helps build trust and credibility, ultimately leading to stronger relationships and better business outcomes.
AI email writers can help businesses maintain consistency in their brand voice and messaging. By analyzing previous email interactions and understanding your unique style, AI algorithms can generate content that reflects your company’s values and resonates with your recipients. This level of personalization helps build trust and credibility, ultimately leading to stronger relationships and better business outcomes.
For the Future of Email Writing Technology, it is possible that an Email writer AI can assist non-native English speakers in writing emails with greater confidence and accuracy. By offering real-time suggestions and corrections, AI can help overcome language barriers, ensuring that emails are clear and easily understood by the recipient.
While AI is not yet perfect and may require human oversight in certain situations, the potential it holds for revolutionizing email writing is undeniably exciting. As technology continues to advance, we can expect email writer AI to become increasingly sophisticated, making our lives easier and enhancing our communication in the digital realm.
In conclusion, an email writer AI is revolutionizing the way businesses communicate — check out Clippit AI to start! By leveraging advanced algorithms and machine learning, businesses can now create effective and personalized emails at scale. So, if you’re looking to enhance your communication efforts and save time, consider using AI email writers to take your email game to the next level.
Entertainment in Gangnam — A Hub for Cutting-Edge Fun
 What Makes Gangnam Advanced Entertainment a Must-Visit Destination in Seoul?
What Makes Gangnam Advanced Entertainment a Must-Visit Destination in Seoul?
When it comes to entertainment, Seoul offers a lot of options, but one district that stands out is Gangnam. Known for its vibrant nightlife, luxury shopping, and trendy cafes, Gangnam has become a must-visit destination for locals and tourists alike.
Unveiling the Hidden Gems of Gangnam Advanced Entertainment
Located in the heart of Gangnam, the Gangnam Saraitne Hyperblic is a one-stop destination for all your entertainment needs. Whether you’re into gaming, karaoke, or just looking to have a good time, this entertainment complex has it all. It boasts a wide variety of activities, ensuring that there’s something for everyone to enjoy.
One of the main highlights of Gangnam Saraitne Hyperblic is its state-of-the-art gaming facilities. With the latest equipment and a wide selection of games, both casual gamers and hardcore enthusiasts will find themselves immersed in a world of virtual adventures. There’s also karaoke for music lovers.
강남 사라있네 하이퍼블릭, which translates to “Gangnam disappears, hyper public,” is an immersive entertainment venue that takes visitors on a journey into the realms of augmented reality (AR) and virtual reality (VR). It combines cutting-edge technology with creative storytelling to create an unforgettable experience. From adrenaline-pumping VR games to mind-boggling AR art installations, 강남 사라있네 하이퍼블릭 promises to transport you to a whole new world.
 Another hidden gem in Gangnam’s entertainment scene is the thriving underground music culture. Amidst the mainstream K-pop industry, there are numerous indie music venues and live houses where talented local bands and musicians showcase their skills. These venues, such as Rolling Hall and DGBD, offer a more intimate and authentic experience for music lovers. Whether you’re into rock, jazz, or hip-hop, Gangnam’s underground music scene has something for everyone.
Another hidden gem in Gangnam’s entertainment scene is the thriving underground music culture. Amidst the mainstream K-pop industry, there are numerous indie music venues and live houses where talented local bands and musicians showcase their skills. These venues, such as Rolling Hall and DGBD, offer a more intimate and authentic experience for music lovers. Whether you’re into rock, jazz, or hip-hop, Gangnam’s underground music scene has something for everyone.
Gangnam is also home to unique and unconventional entertainment spots that cater to different interests. From board game cafes to themed escape rooms, the district offers a wide range of activities for friends, families, and even solo adventurers. Places like Escapade, an escape room with a twist of mystery and suspense, or Tabletop, a cafe stocked with hundreds of board games, provide an opportunity to engage with others and have a memorable experience in an unconventional way.
So, if you’re looking to uncover a different side of Gangnam’s entertainment scene, venture beyond the mainstream and explore these hidden gems. Whether it’s immersing yourself in the world of AR and VR at 강남 사라있네 하이퍼블릭 or discovering talented indie musicians at live houses, Gangnam has much more to offer than meets the eye. Step off the beaten path, and you might just find yourself creating unforgettable memories in this vibrant district.
The Importance of Fort Worth Gate Repair Fences and Gate Services
 Are you tired of grappling with a faulty gate that refuses to open or close smoothly? Or perhaps your fence has seen better days, with cracks and gaps that compromise both security and aesthetics? If so, you’re not alone. Many homeowners in Fort Worth, Texas, face these frustrating and potentially dangerous gate and fence issues. The good news is that there are gate repair fences and gate services available that can breathe new life into your property and provide the security and peace of mind you deserve. In this article, we will explore the importance of Fort Worth gate repair fences and gate services, and why investing in these essential services is both practical and beneficial for homeowners. So, lets discover how Fort Worth gate repair fences and gate services can transform your property for the better.
Are you tired of grappling with a faulty gate that refuses to open or close smoothly? Or perhaps your fence has seen better days, with cracks and gaps that compromise both security and aesthetics? If so, you’re not alone. Many homeowners in Fort Worth, Texas, face these frustrating and potentially dangerous gate and fence issues. The good news is that there are gate repair fences and gate services available that can breathe new life into your property and provide the security and peace of mind you deserve. In this article, we will explore the importance of Fort Worth gate repair fences and gate services, and why investing in these essential services is both practical and beneficial for homeowners. So, lets discover how Fort Worth gate repair fences and gate services can transform your property for the better.
Key Reasons to Prioritize Fort Worth Gate Repair Fences and Gate Services
When it comes to ensuring the safety and security of your property, prioritizing Fort Worth gate repair fences and gate services is essential. A sturdy and well-maintained gate provides a strong line of defense against intruders and unwanted visitors. Here are the key reasons why you should make gate repair a top priority.
1. Your Property Security can be Compromised
Firstly, a damaged or malfunctioning gate can compromise the security of your property. A gate that doesn’t close or latch properly can easily be exploited by trespassers, putting your belongings and loved ones at risk. By investing in Fort Worth gate repair services, you can ensure that your gate is fully functional and provides the protection you need.
2. Proper maintenance can prolong lifespan of your gate/fence
Secondly, regular gate maintenance and repair can help prolong its lifespan. Gates are exposed to various weather conditions, which can cause wear and tear over time. By addressing any issues promptly, such as rust, loose hinges, or broken parts, you can prevent further damage and extend the life of your gate.
 3. Your property will have improved style
3. Your property will have improved style
Lastly, improving the aesthetics of your property is another significant benefit of gate repair services. A well-maintained gate contributes to the overall curb appeal of your home or business. With the help of Fort Worth gate repair experts, you can restore the beauty and elegance of your gate, enhancing the value of your property.
In conclusion, prioritizing Fort Worth gate repair fences and gate services is crucial for several reasons. It ensures the safety and security of your property, extends the lifespan of your gate, and enhances the overall aesthetics of your home or business. Don’t delay in addressing any gate issues – invest in professional gate repair services to enjoy these benefits and ensure peace of mind. Contact them now!
Harnessing Cubaris Isopods for Technological Advancements and Enhanced Security Measures

Introduction to Cubaris Isopods
Cubaris isopods, also known as miniature armadillo bugs or dwarf white isopods, are small crustaceans belonging to the family Cubaridae. These fascinating creatures have gained attention not only for their unique appearance but also for their potential in various technological and security applications.
Natural Habitat and Characteristics
Cubaris isopods are primarily found in humid environments such as tropical forests, where they inhabit leaf litter and decaying organic matter. They possess a distinctive armored exoskeleton, which provides protection against predators and environmental conditions. Their ability to thrive in diverse habitats makes them resilient and adaptable organisms.
Role in Technological Advancements
Cleaning Technologies
One of the notable contributions of Cubaris isopods is in the field of cleaning technologies. These organisms are efficient decomposers, feeding on organic waste and debris. As a result, they play a crucial role in natural waste management processes. Researchers are exploring the potential of harnessing Cubaris isopods for bio-based cleaning solutions, offering an eco-friendly alternative to traditional methods.
Biomedical Applications
Cubaris isopods exhibit unique physiological properties that make them promising candidates for biomedical applications. Studies have shown that certain compounds found in their exoskeleton possess antimicrobial properties, which could be utilized in the development of antimicrobial coatings for medical devices. Additionally, their regenerative abilities are of interest to researchers investigating tissue regeneration and wound healing.
Environmental Monitoring
Due to their sensitivity to environmental changes, Cubaris isopods are valuable indicators of ecosystem health. Monitoring their behavior and population dynamics can provide insights into the impact of environmental pollutants and habitat degradation. Integrating isopods into environmental monitoring systems could enhance our ability to assess and mitigate ecological threats.
Enhanced Security Measures
Detection of Hazardous Materials
Cubaris isopods possess a remarkable sense of smell, allowing them to detect subtle chemical cues in their surroundings. This sensitivity makes them valuable assets in the detection of hazardous materials such as explosives or narcotics. By training isopods to recognize specific odors, security agencies can employ them in scent-based detection systems for enhanced security screening.
Surveillance and Detection Systems
In addition to their olfactory capabilities, Cubaris isopods exhibit keen sensory perception, particularly in response to vibrations and movements. This attribute can be leveraged in surveillance and detection systems, where isopods are equipped with miniature sensors to detect intrusions or unauthorized activities. Their small size and inconspicuous nature make them ideal for covert surveillance operations.
Security Breach Prevention
Deploying Cubaris isopods in sensitive areas can act as a deterrent against security breaches. Their presence serves as a natural barrier, deterring potential threats while providing continuous monitoring capabilities. Furthermore, their ability to navigate complex environments enables them to access areas that may be challenging for conventional security measures.
Research and Development Efforts
Ongoing research efforts are focused on further understanding the biology and behavior of Cubaris isopods to unlock their full potential in technological and security applications. Collaborative initiatives between academia, industry, and government agencies are driving innovation in isopod-based technologies, paving the way for novel solutions to pressing challenges.
Future Prospects and Challenges
The future of harnessing Cubaris isopods for technological advancements and enhanced security measures holds great promise. However, several challenges must be addressed, including ethical considerations, regulatory frameworks, and technological limitations. Continued investment in research and development is essential to overcome these challenges and realize the full potential of these remarkable creatures.
Also read: Tech-Infused Cleanliness: Revolutionizing Cleaning Services in Singapore
Conclusion
In conclusion, Cubaris isopods represent a unique intersection of biology and technology, offering versatile solutions for cleaning technologies, biomedical applications, and security measures. Their adaptability, sensory capabilities, and eco-friendly nature make them valuable assets in various domains. By harnessing the potential of Cubaris isopods, we can advance both technological innovation and security enhancement efforts.
Protecting Your IPTV Subscription: Understanding Security Risks and Best Practices

Internet Protocol Television (IPTV) has transformed how we access television content in today’s digital age. With the convenience of on-demand streaming and access to a plethora of channels, IPTV subscriptions have become increasingly popular. However, amidst the convenience lies a lurking threat – security risks that could compromise your IPTV experience. Understanding these risks and implementing best practices is crucial to safeguarding your IPTV subscription.
One of the primary security risks associated with IPTV subscriptions is piracy. Unauthorized distribution of copyrighted content not only violates intellectual property rights but also exposes users to legal consequences. Unscrupulous entities often offer cheap or even free IPTV services by illegally streaming copyrighted material. To protect yourself from inadvertently supporting piracy, it’s essential to choose reputable IPTV providers who have obtained proper licensing agreements for the content they offer.
Additionally, data breaches pose a significant threat to IPTV subscribers’ privacy and security. Hackers may target IPTV platforms to gain access to users’ personal information, including payment details and viewing habits. To mitigate this risk, users should prioritize platforms that implement robust security measures, such as encryption protocols and secure payment gateways. Furthermore, regularly updating passwords and being cautious of phishing attempts can help prevent unauthorized access to your IPTV account.
Malware is another pressing concern for IPTV users. Cybercriminals may embed malicious software into IPTV applications or streaming links, compromising users’ devices and stealing sensitive information. To protect against malware, it’s crucial to only download IPTV apps from trusted sources such as official app stores. Additionally, installing reputable antivirus software and conducting regular scans of your devices can help detect and remove any malicious threats.
ALSO READ: The Role of PPC Reseller in Ensuring the Security of Technology Businesses
When it comes to safeguarding your IPTV subscription, adopting best practices is key. Firstly, opt for secure payment methods such as credit cards or reputable digital payment platforms to minimize the risk of financial fraud. Avoid sharing sensitive information, such as account credentials or payment details, with anyone to prevent unauthorized access to your IPTV account.
Furthermore, be cautious of unofficial IPTV providers that offer suspiciously low prices or promise access to premium content for free. These providers often operate outside legal boundaries and may expose users to various risks, including malware infections and unreliable service quality. Instead, opt for established IPTV providers with a track record of reliability and a commitment to protecting users’ security and privacy.
Implementing encryption protocols, such as Virtual Private Networks (VPNs), can add an extra layer of security to your IPTV browsing experience by encrypting your internet connection and masking your IP address. This helps prevent unauthorized surveillance and protects your online activities from prying eyes.
Conclusion
Protecting your IPTV subscription requires a proactive approach to understanding and mitigating security risks. By choosing reputable providers, employing best practices, and staying vigilant against potential threats, you can enjoy a secure and uninterrupted IPTV experience without compromising your privacy or security.
Tech-Infused Cleanliness: Revolutionizing Cleaning Services in Singapore

In the fast-paced city-state of Singapore, the synergy between technology and everyday services is evolving to meet the demands of modern living. Among these services, cleaning has undergone a remarkable transformation, embracing innovative solutions for enhanced security and cleanliness. One standout aspect of this technological integration is the specialized domain of mattress cleaning in Singapore, contributing significantly to the creation of secure living spaces.
The Tech Wave Sweeping Through Cleaning Services
The landscape of cleaning services in Singapore has witnessed a paradigm shift, with technology playing a pivotal role in redefining industry standards. Automated cleaning processes, smart sensors, and data-driven strategies are now commonplace, ensuring a thorough and efficient cleaning experience for residents. This tech wave not only improves the quality of cleaning but also addresses the critical aspect of security.
Automated Efficiency in Cleaning
Automated cleaning devices have become the backbone of modern cleaning services, allowing for precision and efficiency. Robotic vacuum cleaners equipped with advanced sensors navigate spaces seamlessly, leaving no corner untouched. This not only enhances the overall cleanliness but also minimizes the risk of oversight, contributing to a secure environment.
Smart Sensors and Data-Driven Strategies
Smart sensors integrated into cleaning equipment enable a data-driven approach, optimizing cleaning routines based on usage patterns and real-time feedback. This level of sophistication ensures that cleaning services are not only effective but also tailored to the specific needs of each environment. The utilization of data analytics enhances security measures, as irregular patterns can be quickly identified and addressed.
Specialized Services: The Rise of Mattress Cleaning in Singapore
One area where technology has made a significant impact is in the specialized realm of mattress cleaning. Beyond the surface-level cleaning commonly associated with traditional services, advanced methods are employed to address hygiene and security concerns related to mattresses.
UV-C Technology for Mattress Disinfection
The incorporation of UV-C technology has revolutionized mattress cleaning in Singapore. This technology utilizes ultraviolet light to eliminate bacteria, viruses, and allergens that may reside within the mattress. This not only ensures a hygienic sleeping environment but also contributes to the overall security of residents by reducing the risk of exposure to harmful microorganisms.
Anti-Allergen Treatments
With a growing awareness of allergies and respiratory issues, cleaning services now offer specialized treatments to address allergens present in mattresses. These treatments not only enhance the health aspects of living spaces but also contribute to the overall security and well-being of residents, especially those prone to allergies.
Advancements in Cleaning Technology and Security
Beyond the specific domain of mattress cleaning, the overall advancements in cleaning technology contribute significantly to the security of residential spaces in Singapore.
IoT Integration for Real-Time Monitoring
The integration of Internet of Things (IoT) devices allows for real-time monitoring of cleaning processes. From the status of automated cleaning devices to the consumption of cleaning supplies, IoT ensures that cleaning services are not only efficient but also accountable. This level of transparency adds an extra layer of security, as residents can be assured that cleaning protocols are consistently followed.
Secure Access Control Systems
Cleaning services are increasingly incorporating secure access control systems to ensure that only authorized personnel have access to designated areas. This not only protects residents’ privacy but also enhances overall security by preventing unauthorized entry.
The Future of Cleaning Services in Singapore
As technology continues to advance, the future of cleaning services in Singapore looks promising, with a continued emphasis on cleanliness and security.
Sustainable Cleaning Solutions
The integration of sustainable and eco-friendly cleaning solutions is on the horizon. From biodegradable cleaning agents to energy-efficient cleaning equipment, the industry is moving towards a more environmentally conscious approach. This not only benefits the planet but also contributes to the overall well-being and security of residents.
Artificial Intelligence for Predictive Cleaning
The incorporation of artificial intelligence (AI) in cleaning services is expected to bring about a shift towards predictive cleaning. AI algorithms can analyze data patterns and predict when and where cleaning is most needed, optimizing resources and ensuring a consistently clean and secure living environment.
Conclusion
In the dynamic city of Singapore, the intersection of technology and cleaning services has paved the way for a new era of cleanliness and security. From the adoption of automated cleaning processes to the specialized domain of mattress cleaning, technology continues to shape the landscape of cleaning services. As advancements in cleaning technology progress, residents can look forward to a future where their living spaces are not only impeccably clean but also inherently secure.
Technology, Security, and Shuttle Services for the Future
 The fusion of technology with traditional services like shuttle transportation is reshaping our experience in remarkable ways. This evolution, however, brings with it a critical need to address cybersecurity concerns.
The fusion of technology with traditional services like shuttle transportation is reshaping our experience in remarkable ways. This evolution, however, brings with it a critical need to address cybersecurity concerns.
Imagine stepping into a shuttle like Copper Mountain shuttle from Denver Airport, where your journey is not just about getting from point A to B, but also about interacting with an array of digital services. From WiFi connectivity to personalized entertainment systems, the integration of technology in shuttle services enhances user experience significantly. But with these advancements, there’s an elephant in the room – security.
The first layer of this challenge is data protection. Shuttle services collect vast amounts of personal data, from location tracking to payment information. Protecting this data against breaches is paramount. Sophisticated encryption methods and robust firewalls are no longer optional but a necessity.
Then there’s the aspect of network security. As shuttles become more connected, the risk of cyber-attacks increases. This isn’t just a matter of safeguarding data, but also ensuring the physical safety of passengers. Imagine the chaos if a hacker were to gain control of a shuttle’s navigation system. Regular security audits and real-time monitoring systems are vital to prevent such scenarios.
The conversation also extends to the responsibility of users. In an era where technology is deeply integrated into everyday services, awareness and education about cybersecurity are crucial. Users must be vigilant about the data they share and the networks they connect to while using shuttle services.
Furthermore, regulatory frameworks need to keep pace with technological advancements. Governments and industry bodies must work together to establish standards and guidelines that ensure the safe and secure operation of tech-enhanced shuttle services.
Technology, security, and shuttle services exciting frontier with immense potential. By prioritizing cybersecurity, we can not only enhance the efficiency and enjoyment of shuttle services but also safeguard the trust and safety of users. As we continue to innovate, let’s ensure that security remains at the heart of this technological revolution.
Securing Your Webtoon Wonderland: A Comprehensive Guide to Platform Security
Securing your online presence is paramount. Whether you’re a seasoned webtoon creator or just starting your journey, ensuring the safety and integrity of your webtoon platform is crucial. In this comprehensive guide, we will dive into the security of webtoon platform, offering you invaluable insights and actionable tips to safeguard your webtoon wonderland. Let’s embark on this journey together to protect your creative space and maintain the trust of your audience.
Understanding the Importance of Webtoon Platform Security
Webtoon Wonderland is not just a creative outlet; it’s a dynamic ecosystem where artists and fans converge. Ensuring the security of your platform is not merely a technical concern; it’s about safeguarding your reputation, user data, and content. Here’s why it matters:
1. Preserving Trust
Maintaining trust with your audience is essential for any webtoon creator. A secure platform reassures your readers that their personal information and interactions are protected, fostering a sense of safety and reliability.
2. Protecting Intellectual Property
Your webtoon creations are your intellectual property. A robust security system safeguards your content from unauthorized access or distribution, preventing potential infringement.
3. Data Privacy Compliance
Adhering to data privacy regulations such as GDPR or CCPA is crucial. A breach of user data can result in legal ramifications and damage to your platform’s reputation.
The Pillars of Webtoon Platform Security
Achieving comprehensive security involves multiple layers of protection. Let’s explore these key pillars:
1. Secure Hosting and Infrastructure
Selecting a reputable hosting provider with strong security measures is your first line of defense. Look for providers that offer SSL certificates, regular backups, and robust firewalls to keep your data safe.
2. Authentication and Authorization
Implement a secure login system for your webtoon platform. Utilize multi-factor authentication (MFA) to add an extra layer of protection. Ensure that users can only access content they are authorized to view.
3. Content Encryption
Encrypt your webtoon content to prevent unauthorized access. Implement encryption protocols like HTTPS to secure data transmission between your platform and users.
4. Regular Software Updates
Outdated software is a common vulnerability. Keep your content management system (CMS) and plugins up to date to patch security flaws.
5. User Education
Educate your users about online security best practices. Encourage strong password usage and provide guidelines on recognizing and reporting suspicious activity.
6. Monitoring and Incident Response
Implement continuous monitoring to detect and respond to security incidents promptly. Have a well-defined incident response plan in place to mitigate potential threats.
Best Practices for Webtoon Creators
As a webtoon creator, you play a pivotal role in maintaining platform security. Here are some best practices to consider:
1. Content Backup
Regularly back up your webtoon content and user data. This ensures that you can recover in case of data loss or security breaches.
2. Content Moderation
Moderate user-generated content to prevent inappropriate or harmful content from appearing on your platform. Implement community guidelines and reporting mechanisms.
3. Regular Security Audits
Conduct periodic security audits to identify vulnerabilities and address them proactively. Engage security experts if necessary.
4. Emergency Response Plan
Prepare for worst-case scenarios by having a well-documented emergency response plan. This plan should outline steps to take in case of a security breach.
5. User Communication
Keep your users informed about security updates, policy changes, and any potential security incidents. Transparency builds trust.
Want to learn morea bout technology and security? You might also be interested in reading Unmasking the Risks: Exploring the Tech and Security Implications of Buying Instagram Followers.
Conclusion
Securing your webtoon wonderland is an ongoing commitment to the safety and satisfaction of your audience. By prioritizing platform security, you not only protect your creative space but also cultivate a loyal following. Remember, the security of your webtoon platform is as important as the stories you share.
Unmasking the Risks: Exploring the Tech and Security Implications of Buying Instagram Followers

One of the most sought-after currencies is the number of followers one has. The allure of a massive Instagram following can be irresistible, and for some, the temptation to buy followers is all too real. While this practice may seem harmless on the surface, it hides a world of tech and security risks that can have far-reaching consequences. In this article, we delve into the dark side of buying Instagram followers, shedding light on the dangers it poses to both individuals and the broader online community.
The Temptation of Buying Instagram Followers
Social media influencers, businesses, and individuals seeking to boost their online presence often contemplate buying Instagram followers as a shortcut to success. It can seem like a simple solution to instantly inflate follower counts, thereby appearing more influential and reputable. However, beneath this façade of popularity lie a myriad of risks.
The Tech Behind Fake Followers
1. Bot Accounts
Many providers of fake followers employ automated bot accounts to fulfill their services. These bots can exhibit erratic behavior, engage in spammy activities, and potentially compromise your account’s security. They can also be used for more nefarious purposes, such as spreading malware or conducting phishing attacks.
2. Algorithmic Red Flags
Instagram’s algorithms are designed to detect suspicious behavior, including sudden spikes in followers. Buying followers can trigger these algorithms, potentially leading to account suspensions or bans. Your account’s visibility and reach can also be negatively impacted, defeating the purpose of acquiring followers in the first place.
Security Concerns
1. Data Privacy
When you purchase followers, you may be sharing sensitive personal and financial information with shady service providers. This opens the door to identity theft and unauthorized use of your data.
2. Account Hijacking
Accounts that buy followers are often targeted by hackers seeking to gain control. Once they have access, they can misuse your account for fraudulent activities or distribute harmful content.
3. Reputation Damage
When your followers discover that you’ve bought fake accounts, it can lead to a significant loss of credibility and trust. Building a genuine and engaged audience takes time and effort, and shortcuts can have lasting consequences.
The Broader Consequences
Beyond individual risks, the practice of buying Instagram followers undermines the integrity of social media platforms and the online community as a whole. It perpetuates a culture of inauthenticity, where metrics are prioritized over genuine connections. This can diminish the value of social media as a platform for communication, engagement, and influence.
You might also want to read about The Intersection Of Technology & Security In The Pneumatic Fittings Manufacturing Industry.
Conclusion
In the quest for online popularity, it’s essential to recognize that buying Instagram followers is a risky endeavor with far-reaching tech and security implications. Instead of chasing numbers, it’s better to focus on creating authentic and meaningful content that resonates with a genuine audience. Building a real following may take time, but it’s a more secure and sustainable path to success in the digital age.
Enhancing Home Gardening with High-Tech Hanging Plant Systems
 The popularity of indoor gardening has soared, with more and more people embracing the beauty and benefits of houseplant hanging in their homes. One fascinating trend is the use of high-tech hanging plant systems. These innovative solutions combine technology and horticulture to create stunning displays while providing convenience and efficiency. Let’s delve into the world of smart hanging plant systems and explore how they can elevate your home gardening experience.
The popularity of indoor gardening has soared, with more and more people embracing the beauty and benefits of houseplant hanging in their homes. One fascinating trend is the use of high-tech hanging plant systems. These innovative solutions combine technology and horticulture to create stunning displays while providing convenience and efficiency. Let’s delve into the world of smart hanging plant systems and explore how they can elevate your home gardening experience.
As urban living spaces become smaller, homeowners and apartment dwellers are seeking creative ways to incorporate greenery into their environments. Smart hanging plant systems have quickly gained traction due to their ability to maximize vertical space and create a striking visual impact. These systems utilize advanced technologies to automate and simplify the care of hanging plants.
The Benefits of High-Tech Hanging Plant Systems
Space Optimization: Vertical gardening is a practical solution with limited floor space. Smart hanging plant systems allow you to make the most of vertical areas, transforming empty walls into lush green installations.
Convenience and Efficiency: Traditional plant care can be time-consuming and challenging for busy individuals. Smart systems automate watering, nutrient distribution, and lighting, ensuring that your plants receive optimal care without constant manual intervention.
Customization and Control
High-tech hanging plant systems often feature smartphone connectivity and intuitive control interfaces. This allows you to adjust lighting schedules, monitor plant health metrics, and receive notifications when it’s time to water or fertilize, all from the convenience of your phone.
Sustainability
Many smart systems integrate energy-efficient LED lighting, ensuring that plants receive the right amount of light while minimizing energy consumption. Some systems also employ water-saving technologies, reducing water waste and promoting eco-friendly practices.
Innovative Features and Technologies
Automated Watering Systems: Smart hanging plant systems utilize sensors to monitor soil moisture levels and deliver the water needed, preventing over or under-watering.
Nutrient Dispensing: These systems can automate the distribution of plant nutrients, ensuring that your plants receive the ideal balance of fertilizers for healthy growth.
Integrated LED Lighting: High-quality LED lights provide the perfect spectrum of light for optimal plant growth. Some systems offer customizable lighting schedules to mimic natural sunlight, promoting photosynthesis and enhancing plant vitality.
Plant Health Monitoring: Sensors embedded within the hanging plant systems can monitor vital metrics such as temperature, humidity, and light intensity. This data is analyzed to provide insights into the overall health of your plants, allowing you to make informed adjustments.
Smart hanging plant systems have revolutionized the way we incorporate greenery into our homes. With their space-saving design, convenience, and customization options, these systems offer an efficient and visually appealing solution for indoor gardening. Whether you’re a busy professional, a gardening enthusiast, or someone with limited space, high-tech hanging plant systems provide an exciting and accessible way to bring nature into your living space. Embrace the future of home gardening with these innovative technologies and enjoy the beauty and benefits of hanging plants like never before.
The Importance Of Technology For Online Shops
Technology has become an integral part of everyday life. It is important for online shops to embrace the latest technology and use it to their advantage.
Online shopping has grown exponentially in recent years, with the majority of consumers now shopping online. Shoppers are looking for more convenience and better experiences than ever before. To meet this demand, retailers of stylish bottles must make use of technology to improve their customer experience and optimize their conversion rates.
How technology can enhance your businesses’ visibility in the marketplace
The technology of the future is creating new ways for businesses to connect with their customers. There are many different ways that technology can help a business to be more visible in the marketplace.
Although these technologies are still in the early stages, they will have a significant impact on how businesses operate and communicate with their customers. For example, instant messaging and chat apps have become increasingly popular in recent years. These apps allow companies to communicate with their clients in an efficient and timely manner while also allowing them to create a community around them.
The first step towards making your business more visible is by understanding what your consumers want from you. The next step is by understanding how your consumers want you to communicate with them so that you can deliver on those needs effectively.

What is the role of technology in stylish bottle online shop marketing?
Technology is becoming a more integral part of the online shopping experience. This is because technology allows you to do many things that were previously impossible. Technology has been an important factor in the success of online shops and these days it’s not just about having a website anymore.
Digital marketing has evolved over time and now encompasses many aspects of human lives ranging from social media, email marketing, content marketing, and search engine optimization to e-commerce. These days it’s not just about having a website anymore. Digital branding and online marketing are important aspects of any business’ success.
What are the benefits of using technology in your e-commerce business?
The benefits of using technology in e-commerce business are many, but they can be broken down into three main categories: productivity, customer experience, and cost savings.
Most important, digital platforms have the power to increase productivity by allowing companies to ship orders faster and reach customers more efficiently. E-commerce is a 24/7 business with customer demands that vary based on time of day, days of the week, and even seasons. By using technology in their operations, retailers can reduce labor costs by automating many manual processes where computers take the burden off humans.
What’s The Importance Of Technology In Website?
Technology has been a big part of life since the beginning. It’s been used to make human lives easier and more convenient. Technology has also helped businesses and platforms such as Submit your article here website grow faster and reach more people.
Technology is important in website design because it helps in creating a website that is user-friendly, interactive, and engaging. It also helps in creating a website that is easy to navigate and increases conversion rates.
Technology can be used in any type of business but it should be considered when designing websites for businesses that are selling products or services online where the customer can interact with the company via email or live chat.
Technology is a key element that every business should have. It can help your business with various tasks, such as marketing, customer service, and content generation.

What is Technology Used for on Websites?
Technology is used on websites for a variety of purposes. It is used to enhance the user experience and increase the performance of websites. It is also used to make websites more engaging and interactive.
How Technology Keeps Websites Secure and Search Engine Friendly
Search engines are the most important way for people to find information online. If your website is not secure, it will be penalized by search engines and you will lose traffic.
There are various ways to keep your website secure and search engine friendly. First of all, you should make sure that all of your content is properly indexed by search engines. This means that the keywords in your content should be relevant to the topic you are writing about. You can also use header tags which help search engines understand what is inside a page before they index it.
Secondly, you should make sure that you have a good amount of social media sharing on your website. This will help increase the visibility of your content and can also lead to more traffic.
Lastly, you should have some sort of blog or article section on your website. This is because blog posts are updated on a regular basis so search engines are more likely to index these fresh pages.









